Microsoft is releasing security baselines for on-premises Active Directory connected devices using group policies. These are used by many organizations around the globe for decades. Using these security settings, administrators can control the state of the corporate devices and maintain the standards. When we are moving device management to the cloud, we can't use group policy settings as group policies are not working in the same way with Azure AD. But now, by using Microsoft Intune security baseline, we can apply Microsoft recommended pre-defined windows security settings to Intune managed Azure AD joined windows 10 devices.
- This is only applicable for devices with Windows 10 version 1809 and later
- You need to have your devices enrolled with Intune with relevant licenses to use this feature. You can find more info about device enrollment using my previous blog posts http://www.rebeladmin.com/2018/11/step-step-guide-enroll-windows-10-devices-microsoft-intune-using-autopilot/
- Microsoft recommended settings are coming with the "Baseline versions". At the moment there is only one baseline version available (MDM Security Baseline for May 2019). But as new windows versions come, there will be new baseline versions.
- When a new baseline version is available, we can migrate already existing security profiles to the new baseline version.
In this blog post, I am going to demonstrate how we can use security baseline policies to enforce security settings.
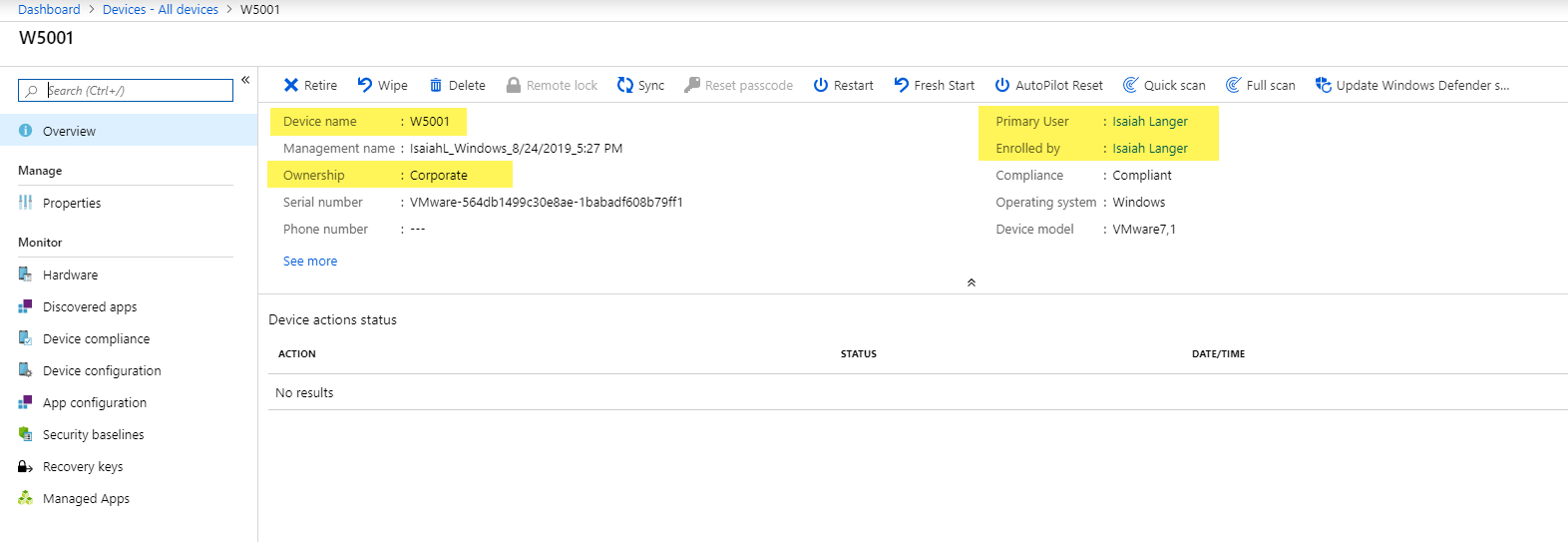
In my demo setup, I have Azure AD joined Windows 10 device called W5001.
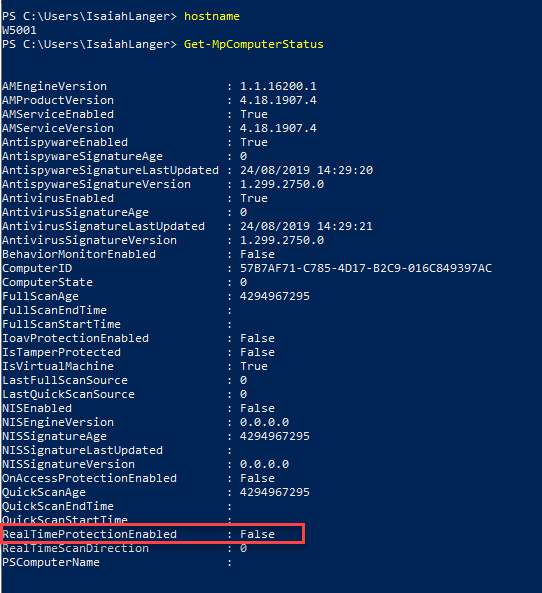
When I log in to this device, I noticed the user has turned off the Windows defender antivirus protection.
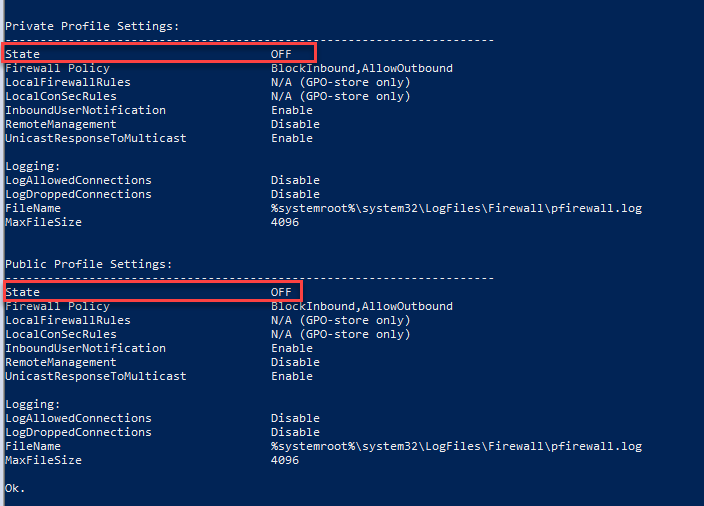
Also, Windows defender firewall is turned off.
As an administrator, I prefer both these services to stay on in all corporate devices. So let's see how we can do this using Intune security baseline policy.
To do that,
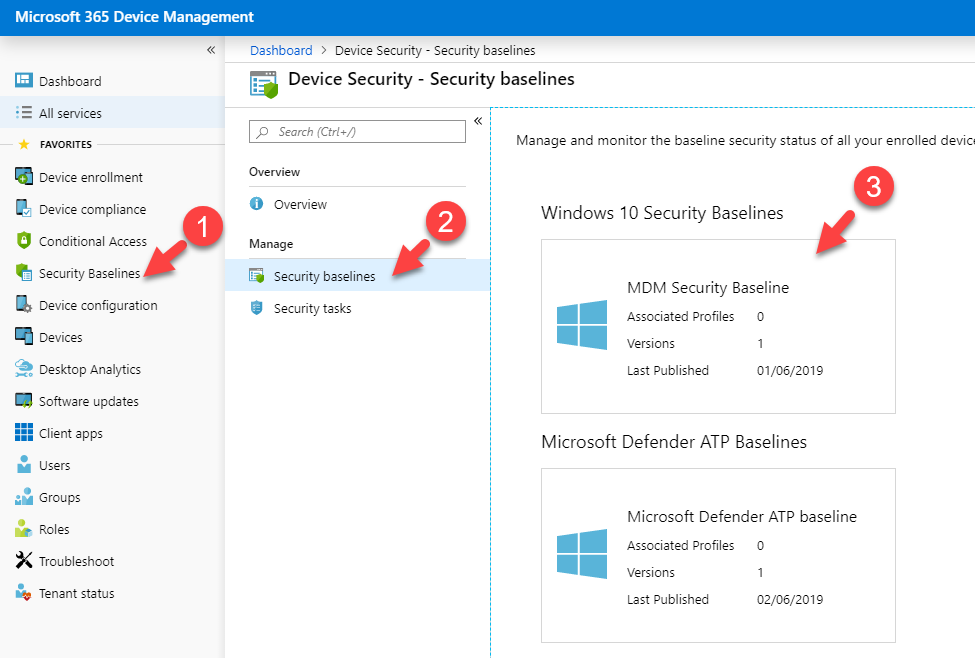
- Log in to Azure Portal (https://portal.azure.com) as Global Administrator and go to All services | Intune or else log in to Intune device management portal directly via https://devicemanagement.microsoft.com
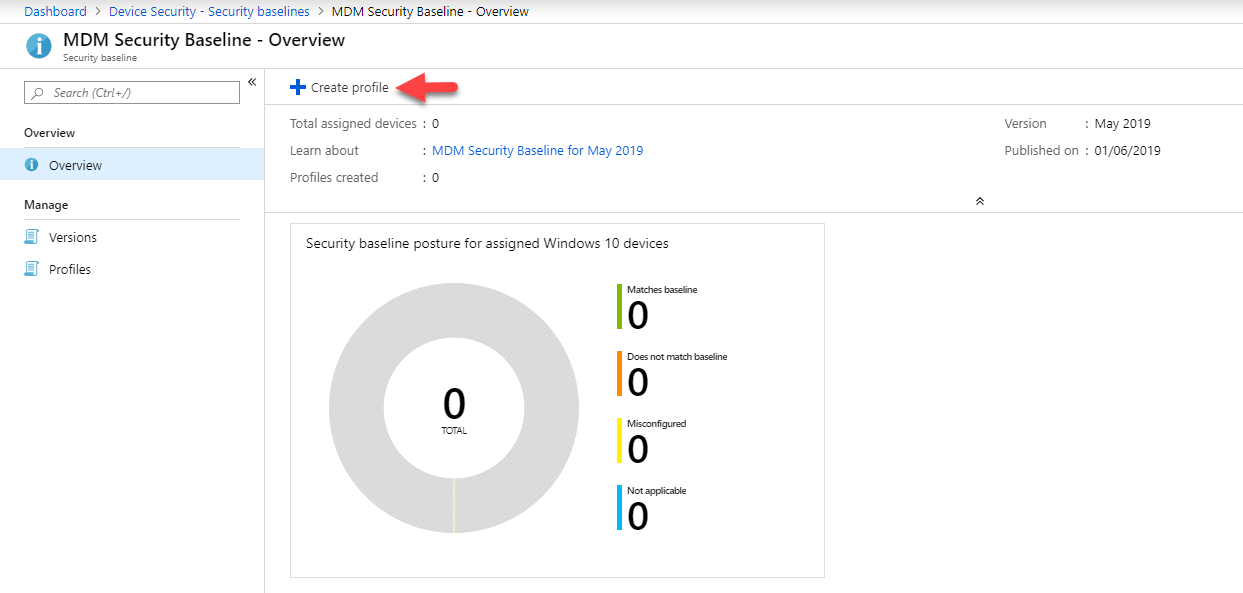
- Then click on Security Baselines | Security baselines | MDM Security Baseline
- Then click on Create profile
- It will open up a new wizard. Provide meaning full name for the profile and click on Next.
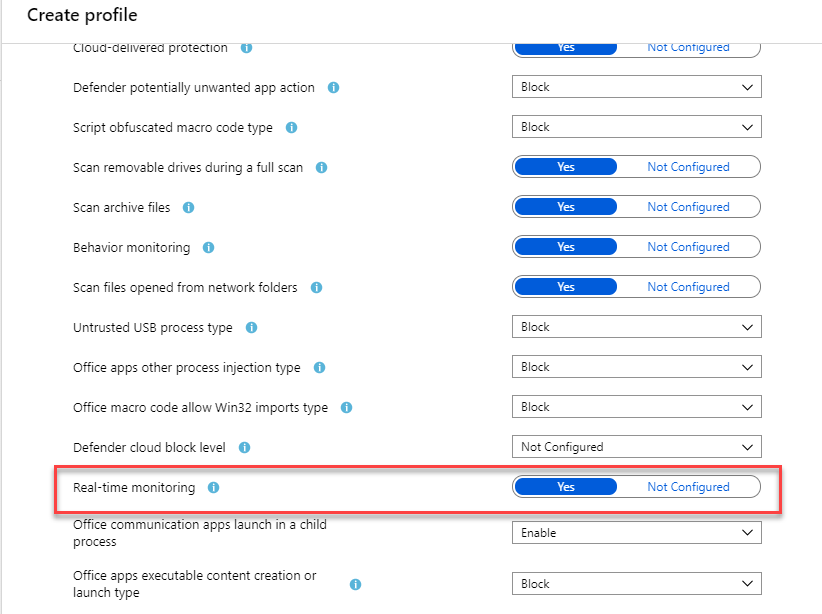
- On the next page, we can see all the settings recommended by Microsoft. We do not need to apply everything. So, go through settings and change according to your corporate requirements. Similar to group policy settings, you can change settings to "Not configured" state if it does not apply to your environment. For our demo, go to Windows Defender Settings and make sure Real-time monitoring is set to Yes.
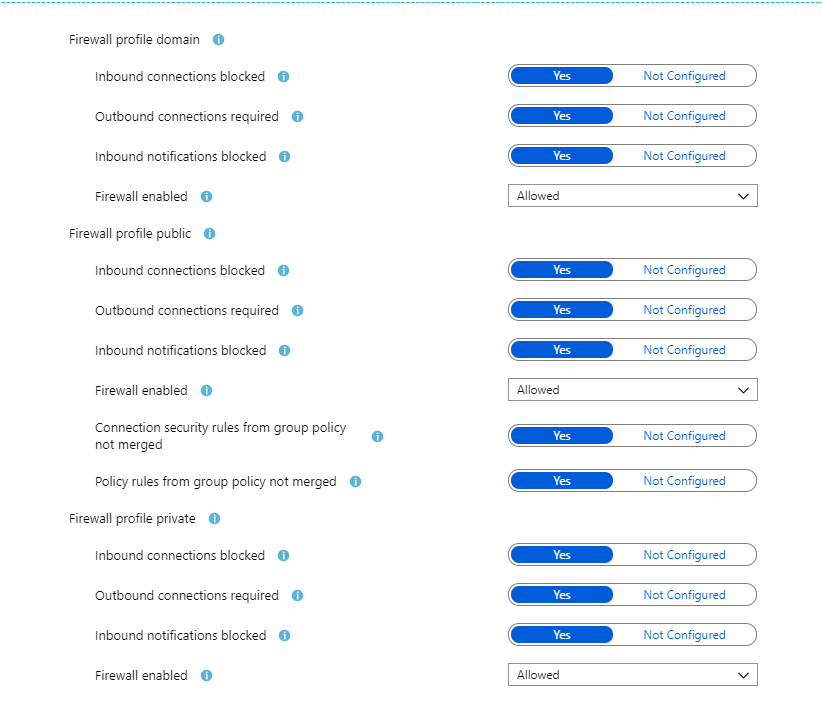
- Then go to Windows Defender Firewall settings and make sure firewall settings are set to Yes.
- Once all the settings are in place click on Next to proceed.
- In scope tags page click on Next as we are not going to use tags.
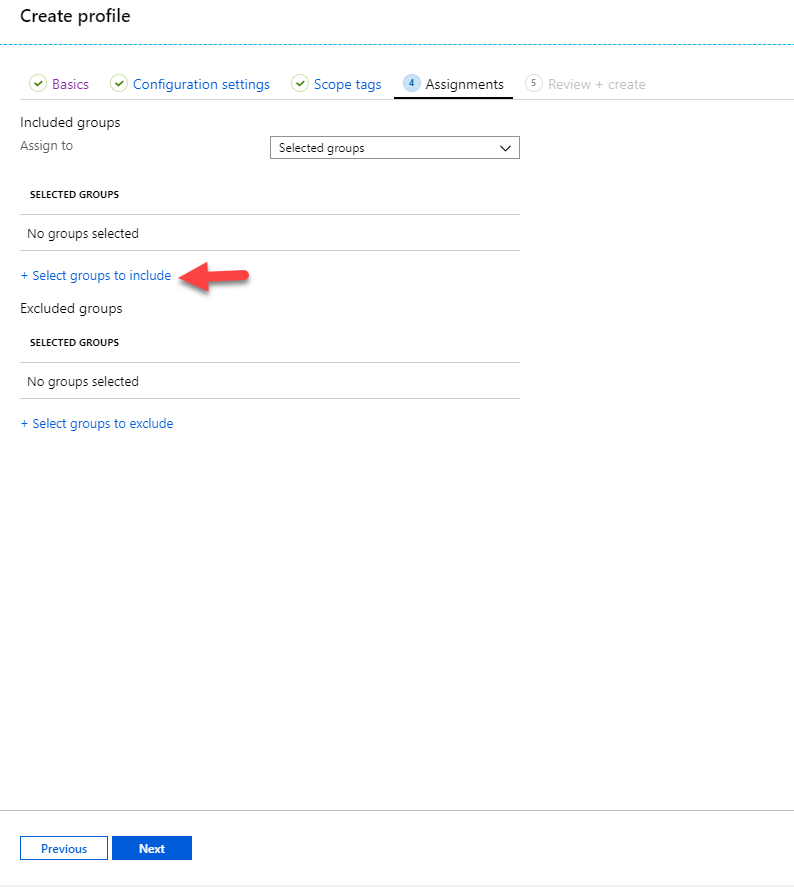
- In the assignments page, we can define the targets. We can apply these settings to Selected Groups, All users, All devices or All users and all devices. In my demo, my users are located in sales and marketing group. So, I am going to use Selected groups option. To select the group, click on Select groups to include option.
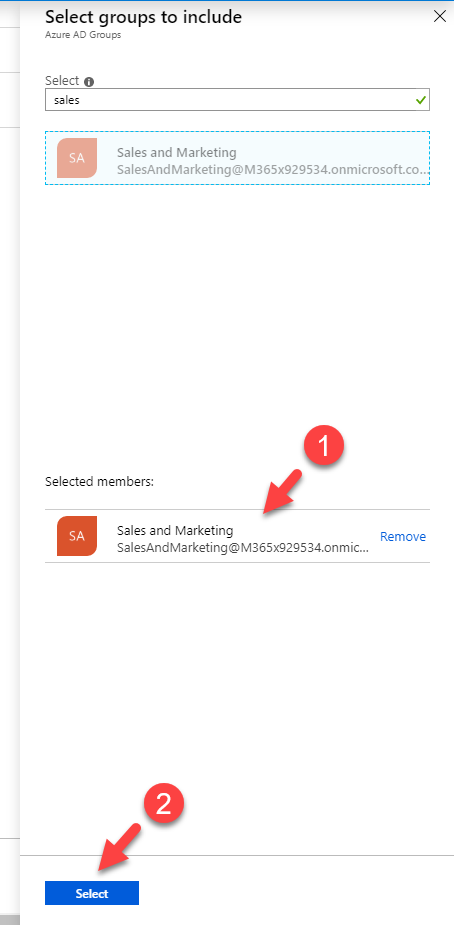
- Then in the new window, search the relevant group. Then click on Select.
- Then click on Next to proceed.
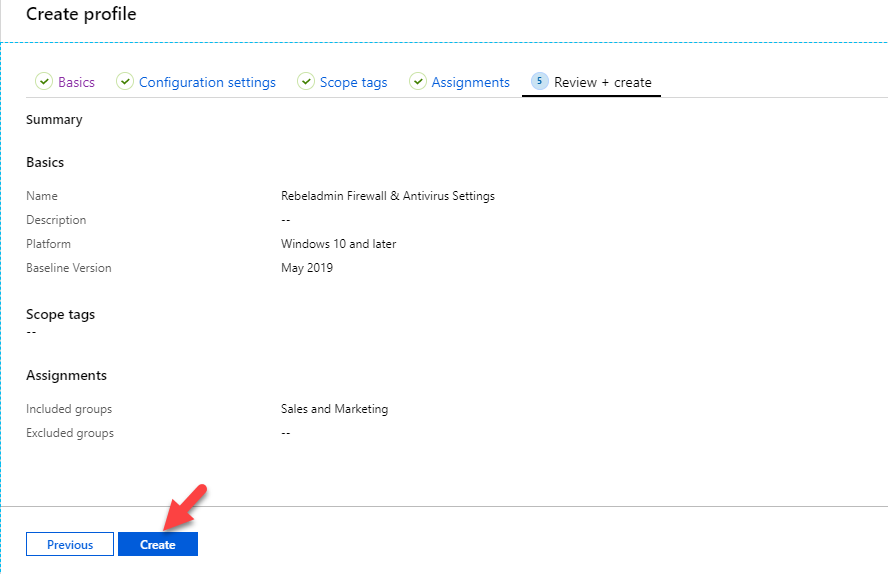
- On the last page, review the settings and click on Create to set up the profile.
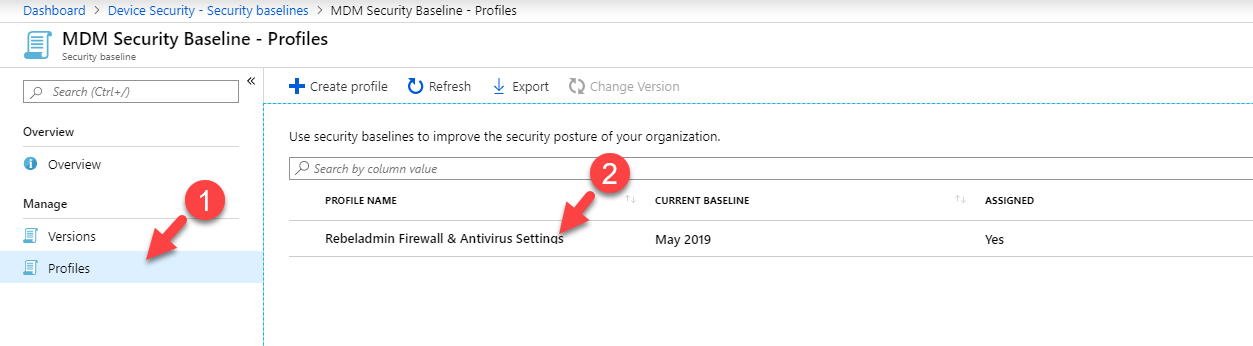
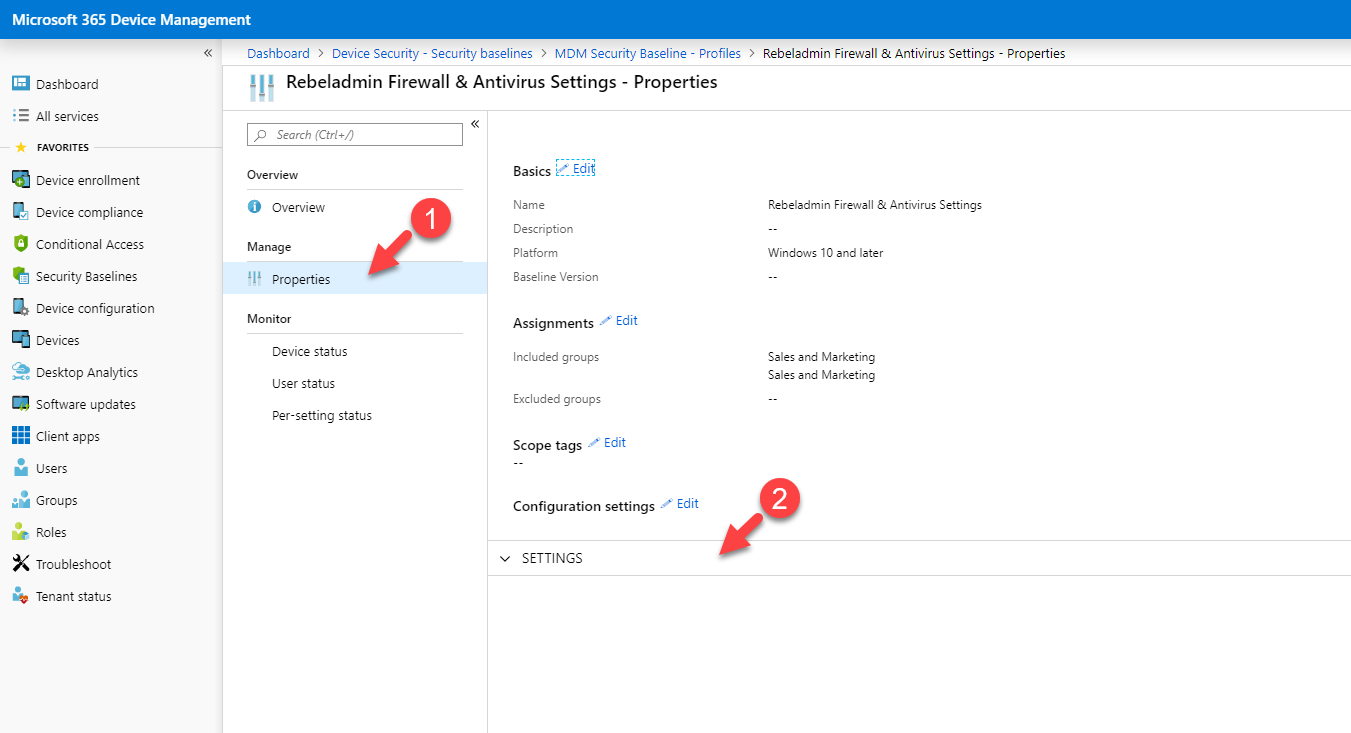
- Once the profile is created, go to MDM Security Baseline and click on the profile we just created. We can find it under Profiles.
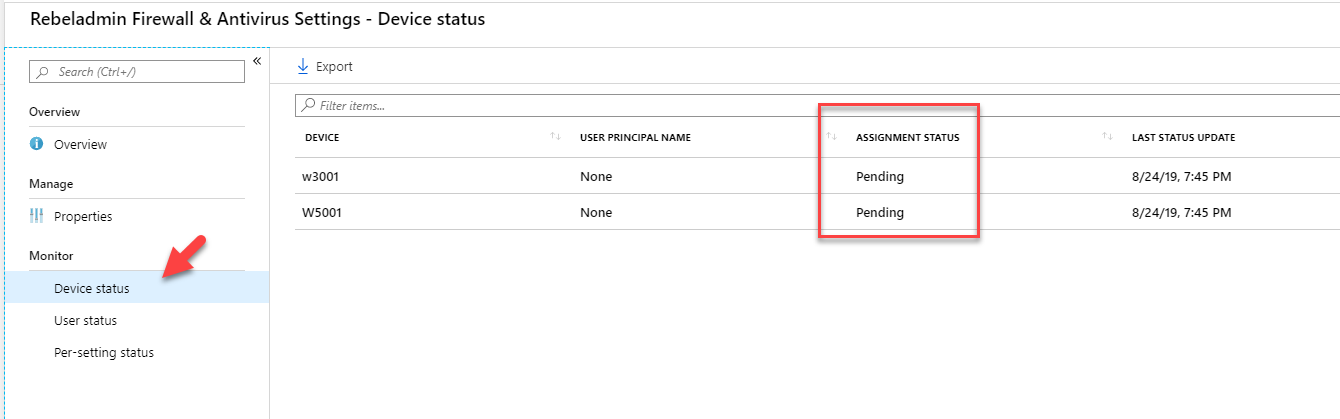
- In the profile page, under the Device status, we can view the status of the policy assignment.
- Also, we can change the policy settings via properties window.
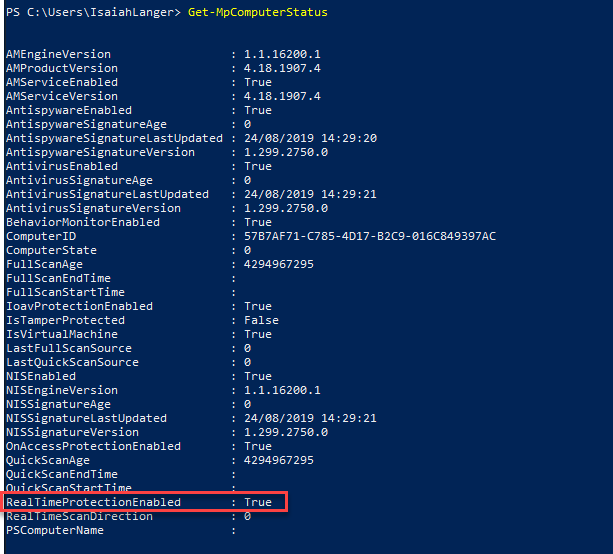
- After several minutes the policy kicks in. when I go to PC now, I can see windows defender antivirus Real-time scanning is enabled.
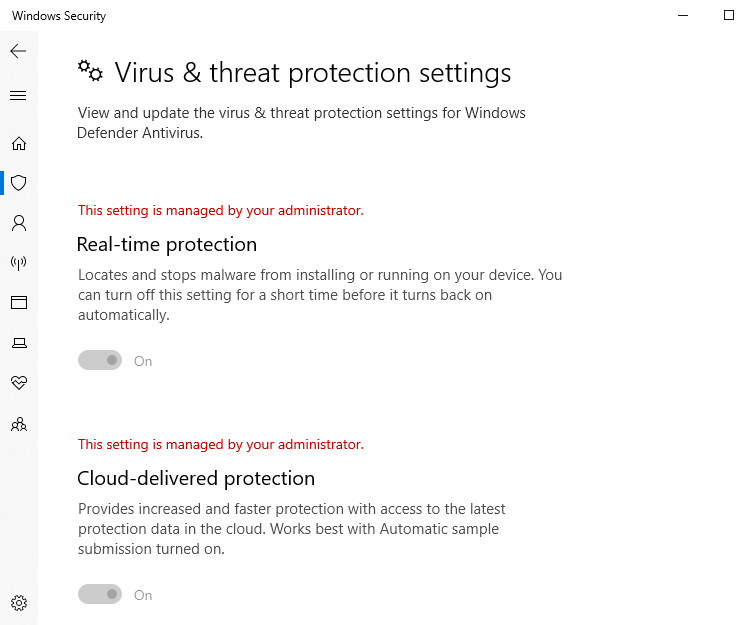
- Also, in settings, it says settings are managed by administrator.
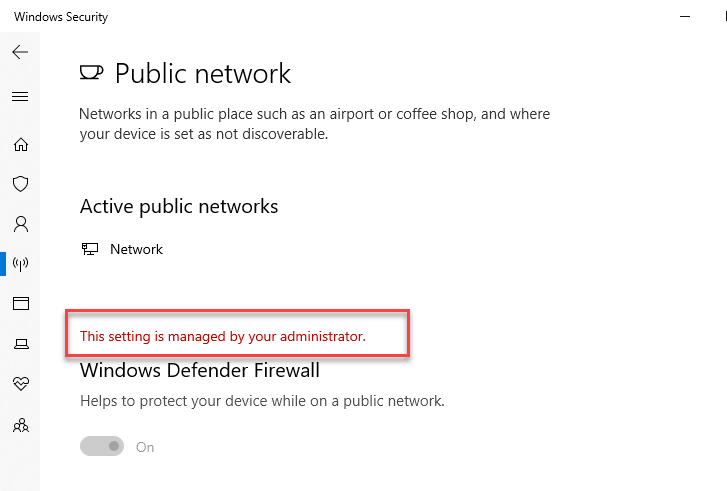
- As expected, Windows defender firewall also now turned on.
As we can see the security baseline settings are applying to the target devices successfully. I hope now you have a better understanding of how intune security baselines can use to enforce security settings across corporate devices. This marks the end of this blog post. If you have any further questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.