This is the part 4 of the series of articles which explains about the AD FS and configuration. If you still not read the part 1, 2 and 3 you can find it here.
Active Directory Federation Services (AD FS) – Part 1
Active Directory Federation Services (AD FS) – Part 2
Active Directory Federation Services (AD FS) – Part 3
In this post let’s look in to some of the components, terms which will be using in AD FS configurations.
Claim based authentication
AD FS communication is works with claim based authentication. Let’s assume, Company A and Company B is business partners. Company A hosts its own CMS (content management system) for company operations. Company B management wants to access this CMS to share business information. So AD FS configuration in Company A can define and allow to make authentication claim from Company B such as “allow CMS access to person form Company B who claims to be from management staff”. AD FS will build a token, based on the above argument. It will include following data.
Claim – Description of an object based on its attributes.
Claim Rules – This includes how AD FS will identify a legitimate claim. For example based on user’s security group membership, users’ email address.
Attribute Store – The storage of the claim values. Usually it is the organization active directory.
Relying Party Trust
Relying party server is a server which host the applications, resources, which need to allow access for the partner organization. In above example the CMS server will be relying party server and partner organization will be Company B. this relying party server will accept and validate the claim tokens provided by the claims provider. Claims provider will be the AD FS server in the network.
To configure relying party trust,
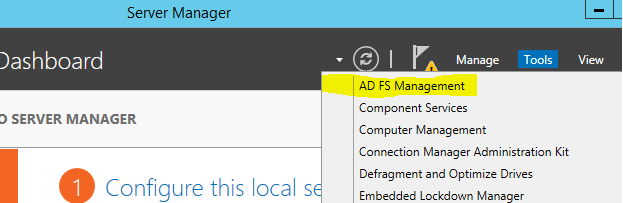
1) Log in to the AD FS server with appropriate permissions (As Domain admin or Enterprise Admin)
2) Server Manager > Tools > AD FS Management
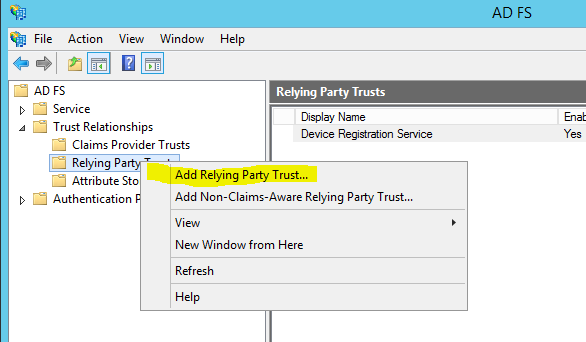
3) Then in AD FS mmc expand AD FS > Trust relationships > Replying Party Trust
4) Then right click and click “Add relying party trust”
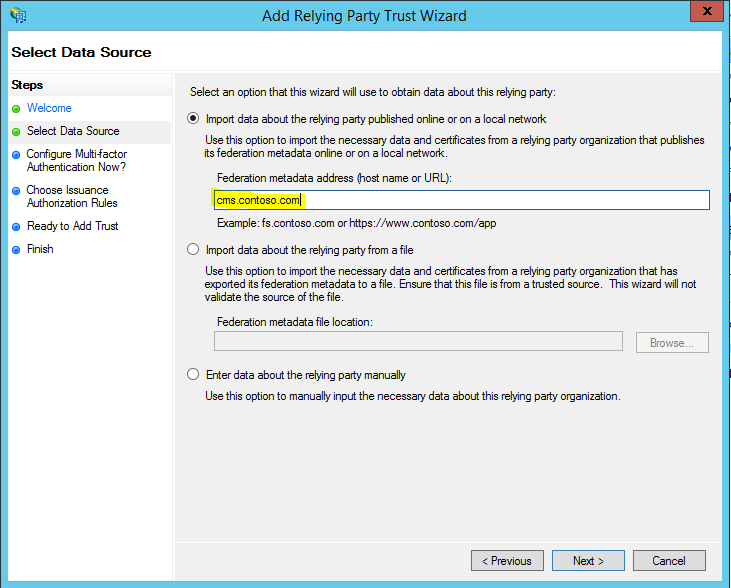
5) It will open up the wizard for adding the relying partner
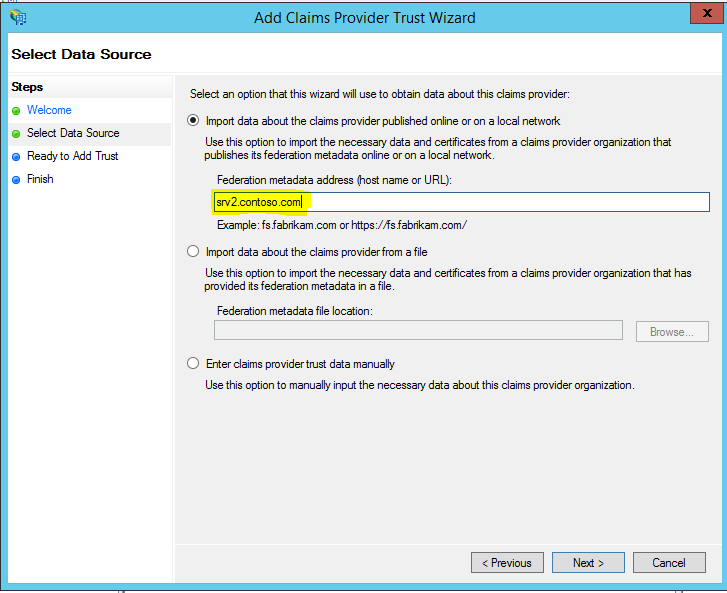
Claims Provider Trust
As explained earlier, AD FS servers are issue claims in the form of tokens. These servers are named as claims providers. If manager A from partner organization wants to access CMS, to prepare the relevant token claims provider will communicate with AD in user’s forest if the authentication is legitimate. Then it will prepare the token based on attributes provided by attribute store.
To configure claims provider trust,
This need to be configure on AD FS which functions as a relying party.
1) Log in to the AD FS server with appropriate permissions (As Domain admin or Enterprise Admin)
2) Server Manager > Tools > AD FS Management
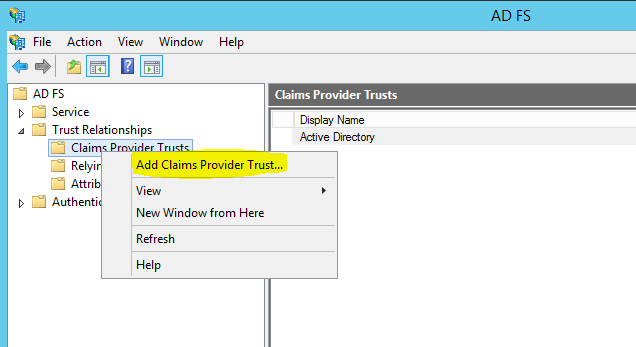
3) Then in AD FS mmc expand AD FS > Trust relationships > Claims Provider Trust
4) Then right click and click “Add claims provider trust”
5) In wizard you can provide the data required
Authentication Policies
Authentication policies will control how AD FS can perform authentication. By default it creates global primary authentication policy.
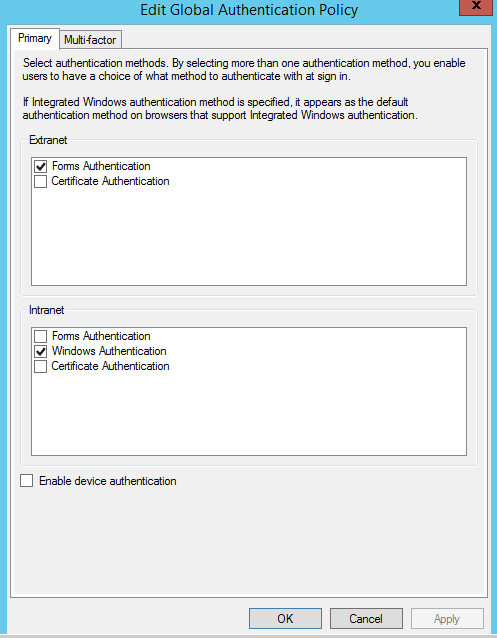
Following authentication methods supports by AD FS
Forms Authentication – Authentication happens on web page. This can be use for internal and external client authentication.
Windows Authentication – Credentials are directly pass to the AD FS via internet explorer or pop-up. This is only available for internal clients.
Certificate Authentication – This will be done based on already provisioned SSL provided by approved CA. this method is available for internal and external clients.
Workplace Join
This feature is available only for windows 2012 R2. It allows to access organization resources via non-domain devices. These devices must running with IOS or windows 8.1. It also needs trusted SSL certificate from 3rd party SSL provider as it will not trust certificates issued by internal CA.
To configure authentication policies,
1) Log in to the AD FS server with appropriate permissions (As Domain admin or Enterprise Admin)
2) Server Manager > Tools > AD FS Management
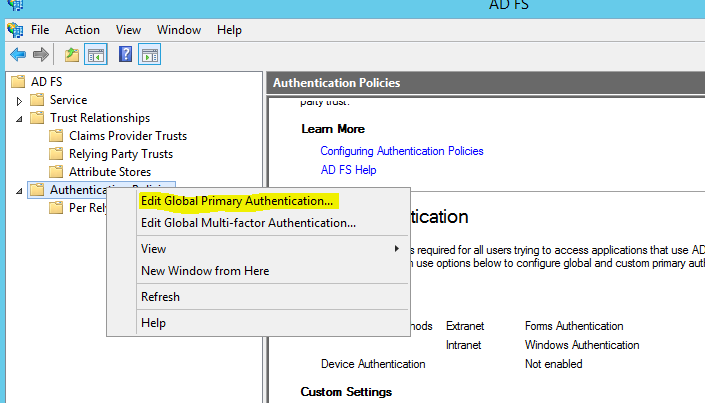
3) Then in AD FS mmc expand AD FS > Authentication Policies.
4) Right click on it and select “Edit Global Primary Authentication”
5) In this window can select required authentication methods. Using option “enable device authentication” will enable workplace join.
This is the end of series of articles explain about AD FS and its configuration. If you have any questions feel free to contact me on rebeladm@live.com