Some time ago I wrote this article about sign-in risk-based conditional access policies. But things have been changed over time and I thought it is time to update it with new content. The updated post can access using https://www.rebeladmin.com/2020/11/step-by-step-guide-how-to-configure-sign-in-risk-based-azure-conditional-access-policies/
In my previous blog posts about conditional access polices I talked about location based and application based polices. In this new blog post I am going to cover risk-based conditional access policies. You can access previous blog posts about conditional access policy using following links,
Step-by-Step Guide to configure location-based Azure conditional access policies – http://www.rebeladmin.com/2018/08/step-step-guide-configure-location-based-conditional-access-policies/
Step-by-Step guide to enable MFA for applications using Azure conditional access – http://www.rebeladmin.com/2018/09/step-step-guide-enable-mfa-applications-using-azure-conditional-access/
Azure AD Identity protection can detect six types of suspicious sign-in activities.
• Users with leaked credentials
• Sign-ins from anonymous IP addresses
• Impossible travel to atypical locations
• Sign-ins from infected devices
• Sign-ins from IP addresses with suspicious activity
• Sign-ins from unfamiliar locations
These six-types of events are categorized in to 3 levels of risks – High, Medium & Low.
|
Sign-in Activity |
Risk Level |
|
Users with leaked credentials |
High |
|
Sign-ins from anonymous IP addresses |
Medium |
|
Impossible travel to atypical locations |
Medium |
|
Sign-ins from infected devices |
Medium |
|
Sign-ins from IP addresses with suspicious activity |
Low |
|
Sign-ins from unfamiliar locations |
Medium |
We can use these risk levels with conditional access policies to protect sensitive application access. In this demo I am going to demonstrate how to create risk-based conditional access policies.
My finance team accessing Microsoft teams’ app remotely. I like to create policy to block access to app if their sign in risk level is detected as High & Medium.
To set up the policies,
1. Log in to https://portal.azure.com
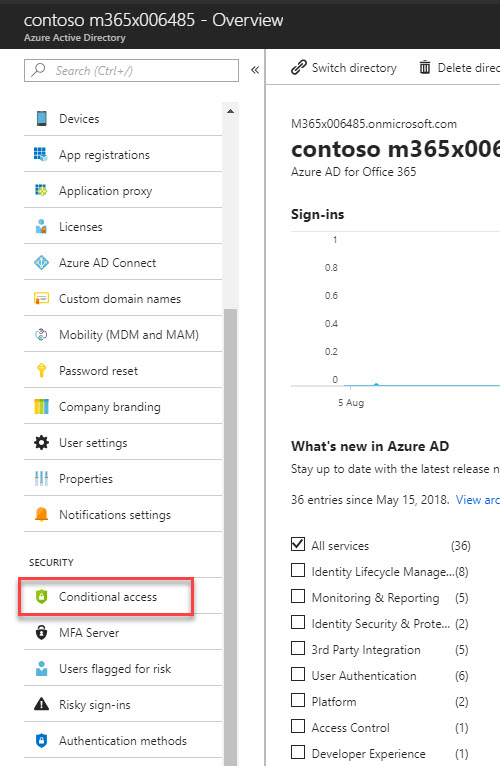
2. Click on Azure Active Directory
3. Click on Conditional access
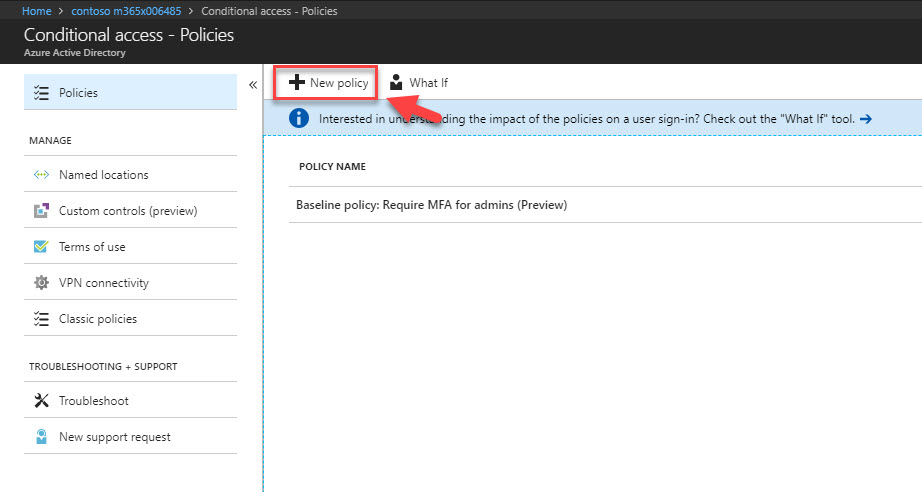
4. In new window, click on New policy to create policy.
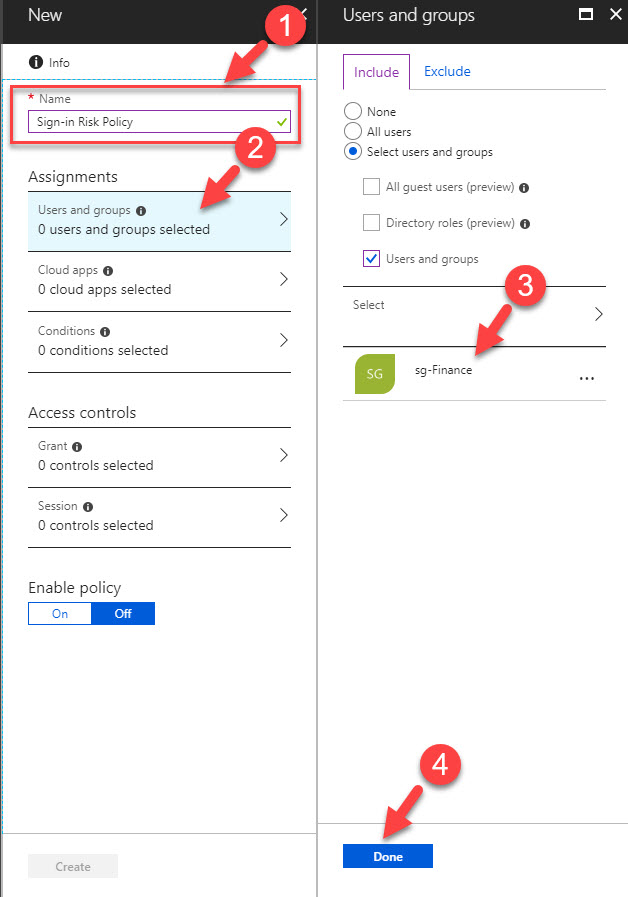
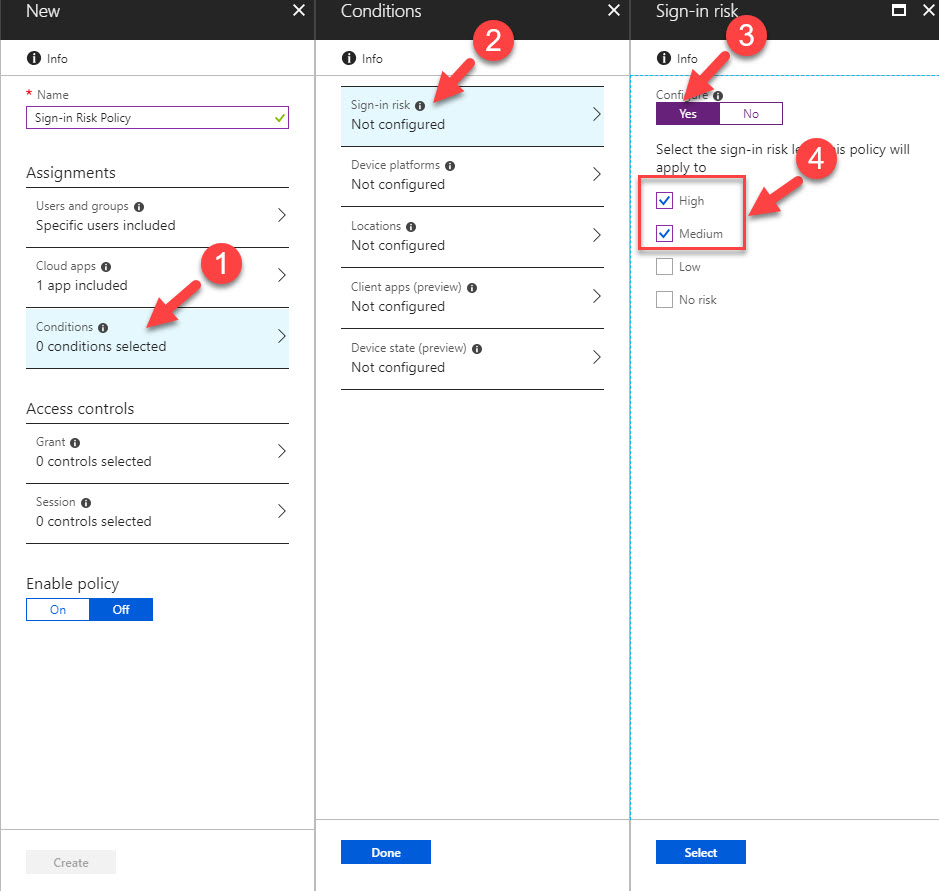
5. In policy window, type name for policy & then click on Users & groups. after I select sg-Finance group.
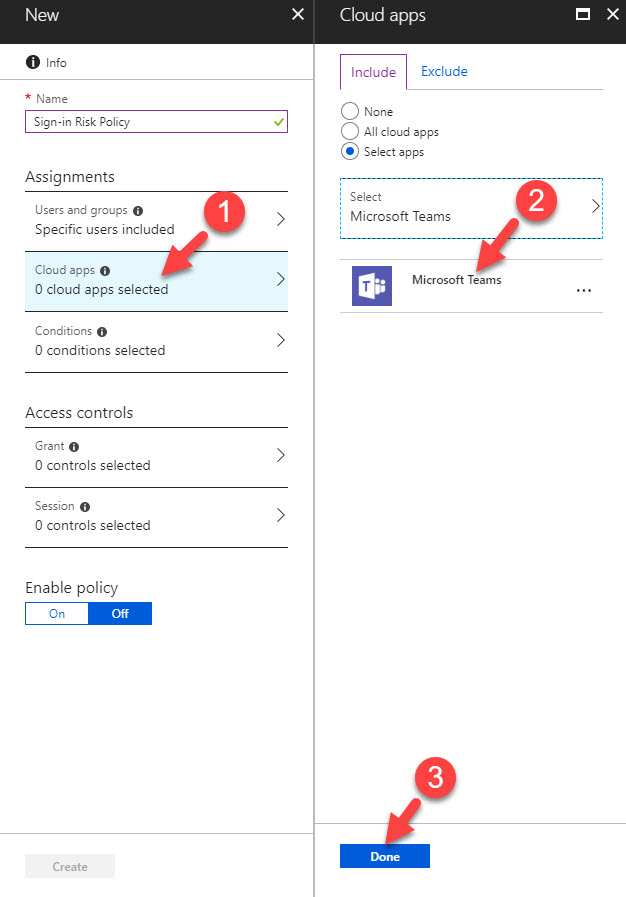
6. Then click on Cloud apps & select Microsoft teams.
7. As next step, click on Conditions | Sign-in risk, then under Configure click on Yes. That will enable sign-in risk policy. We also need to select High & Medium risk levels.
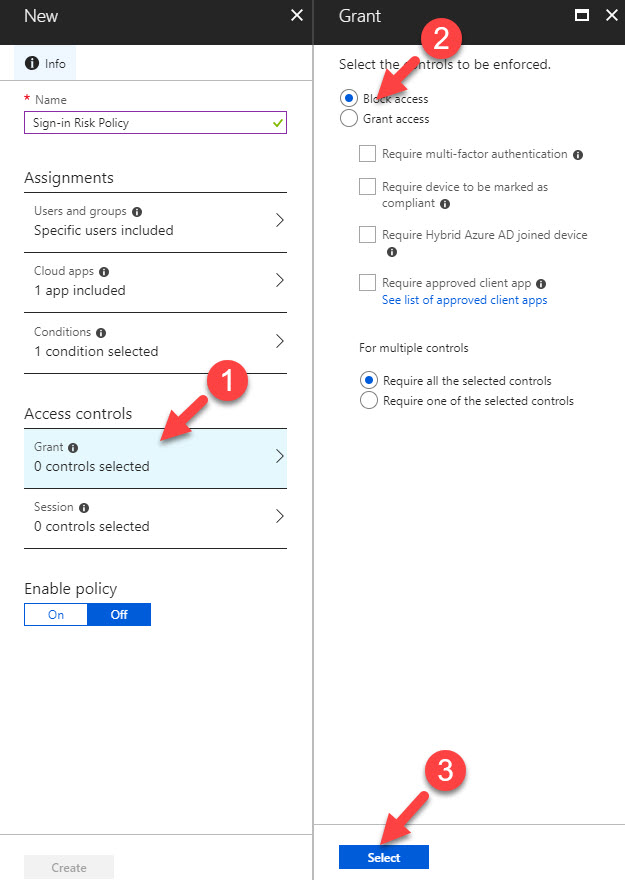
8. Under access control section select Grant, then click on block access.
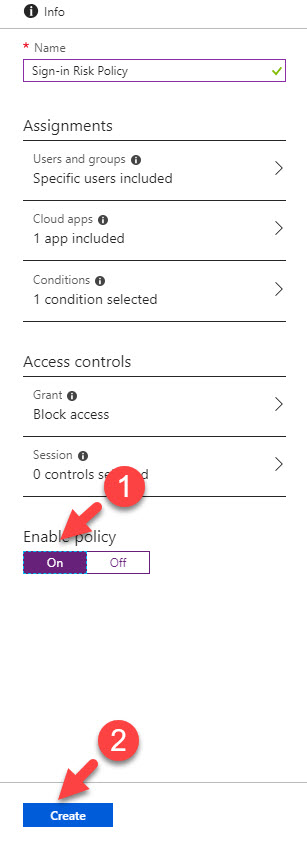
9. At last, click On under enable policy. then click on Create to complete the process.
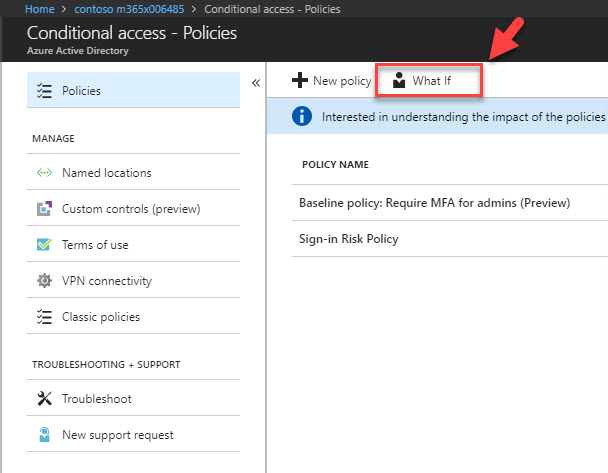
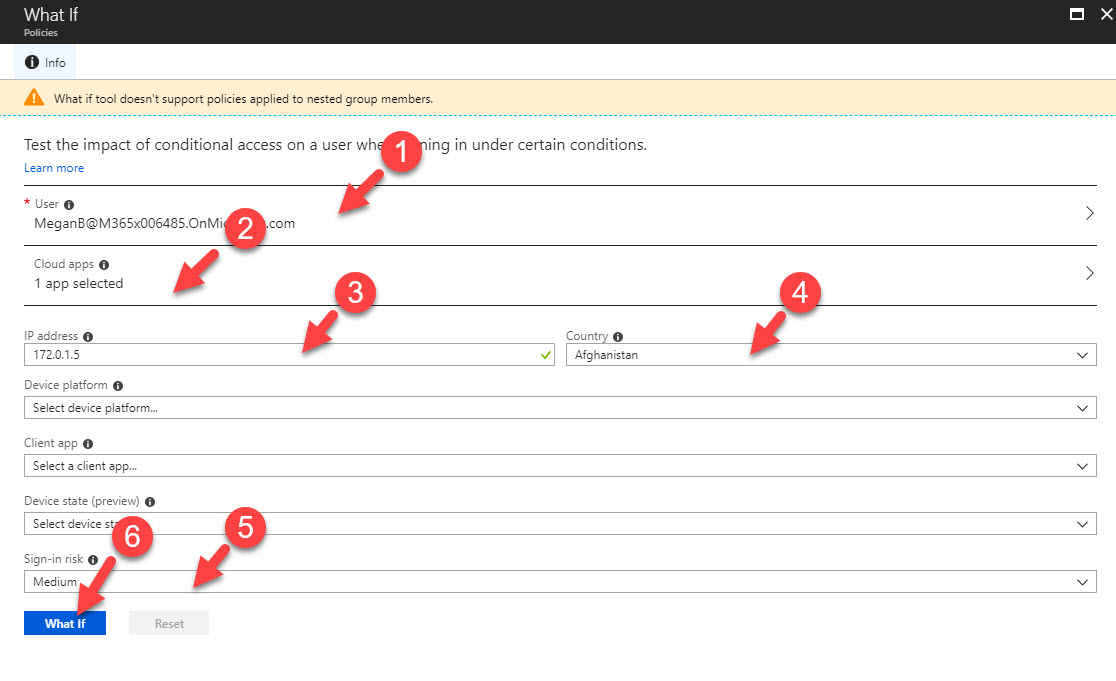
10. Now policy is in place. For testing I am going to use what if feature under conditional access policies. This feature in azure allows to create scenario and see if the policy going to apply as expected. This is the best way to test this type of policies as it is not always practical to create real scenario for testing.
11. To do that, go to Azure Active Directory | Conditional access and then click on what if
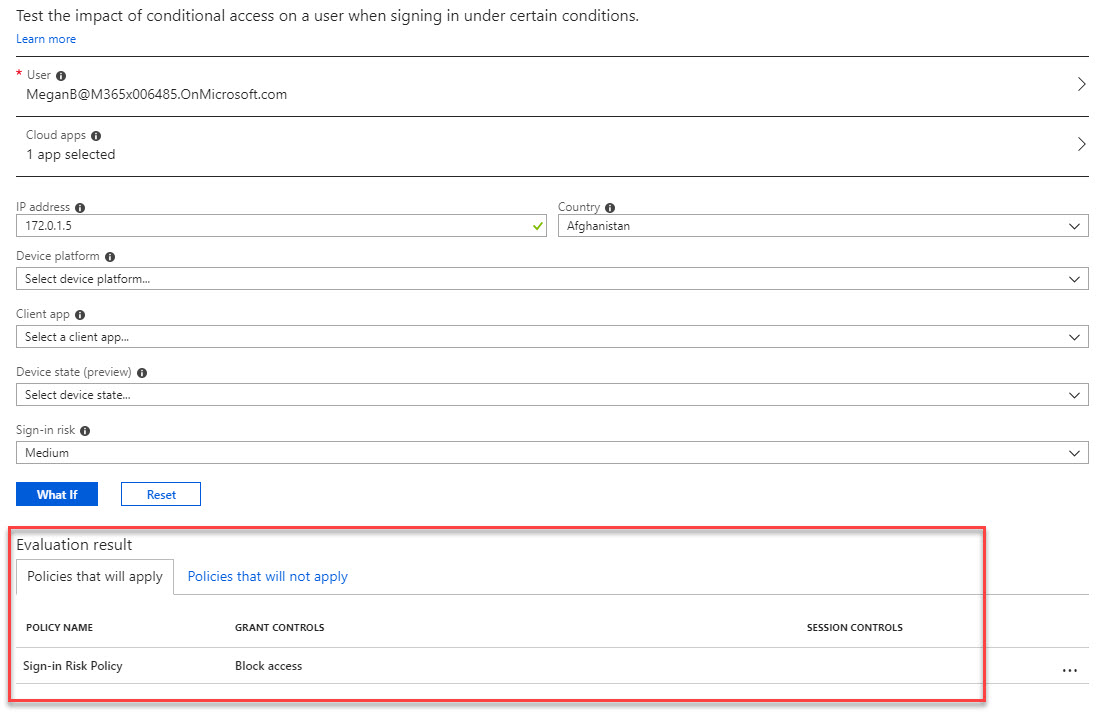
12. In new window, I have selected a demo user from finance team, also selected the Microsoft teams as cloud app. Under IP address I just define dummy ip and select the country Afghanistan. For sing-in risk, I choose medium level. once data is in, we need to click on what if button to complete the test.
13. Once job is executed, result section shows that new policy we just created is applying successfully. This confirms the policy in place is going to work as expected in real world.
This marks the end of this blog post. Hope now you have better understanding how to configure risk-based azure conditional access policies. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.




1 Comment