Azure RMS is the protection technology behind Azure Information Protection (AIP). I have written many articles about Azure RMS & Azure information protection features before but how it really works? what is the technology behind it?
In high-level, I can explain the Azure RMS data protection process as following,
• When a user protects data, Azure RMS will encrypt the content of the file and attach an access policy to it. this policy decides what other users can do with the protected data.
• When other users access the file (after successful Azure AD authentication), Azure RMS will decrypt the file and apply the access policy to it.
In high-level it sounds simple, but let's go through this process in detail to understand the technology behind it.
The best way to understand the technology behind the encryption & decryption process is to go through a scenario. Rebeladmin Inc. employee Andrew is sending a document with sensitive data to another employee Selena. He does not want anyone else in the sales team to have it. So, he is going to use AIP to protect the document. This is the first time both users going to use this solution.
Since this is the first time Andrew and Selena use this AIP, they both need to go through the one-time user environment preparation process. As the first step, Andrew installs the Azure information protection client in his pc. It can be download via https://www.microsoft.com/en-gb/download/details.aspx?id=53018 .
1. Then he authenticates into AIP using his Azure Active Directory Account.
2. After successful authentication, the session will be redirected to the AIP tenant. Then it issues a certificate that will use to authenticate into Azure RMS in the future. This certificate will automatically renew after 31 days by the AIP client. Copy of this certificate will also store in Azure. If the user changes the device, Azure RMS will recreate the certificate using the same keys.
Now the user environment preparation process is done. The next step is to protect the word document.
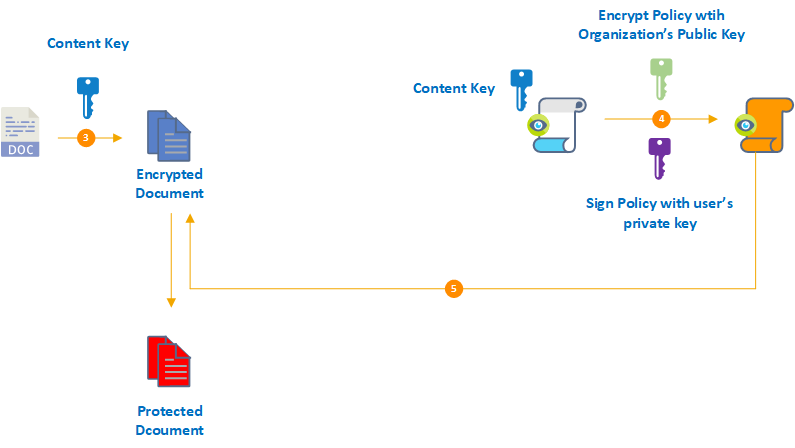
3. Andrew go ahead and request AIP client to protect the document. AIP client creates a random AES key and encrypts the document content using it. This key is called "content key". It uses AES symmetric encryption algorithm. Used key length is 128 bits or 256 bits.
4. Then AIP client creates a policy that contains the access rights for recipient Selena. This can be done using a policy template that is already created by an administrator. Or else users can create ad-hoc policy. Once a policy is in place, the System will encrypt the policy and the symmetric content key using the organization's public key. This key was retrieved by AIP client during the initial user environment preparation process. The policy and the content key are signed by Andrew's certificate which was obtained during the same preparation process.
5. In this step, the AIP client creates a protected document that includes the encrypted document and the policy which is encrypted and signed already.
Once the system creates the protected document, Andrew sent it Selena via email.
Once Selena receives the protect document, she trying to open it. This is the first time she trying to open a protected document. So, she also needs to complete the user environment preparation process before start using AIP.
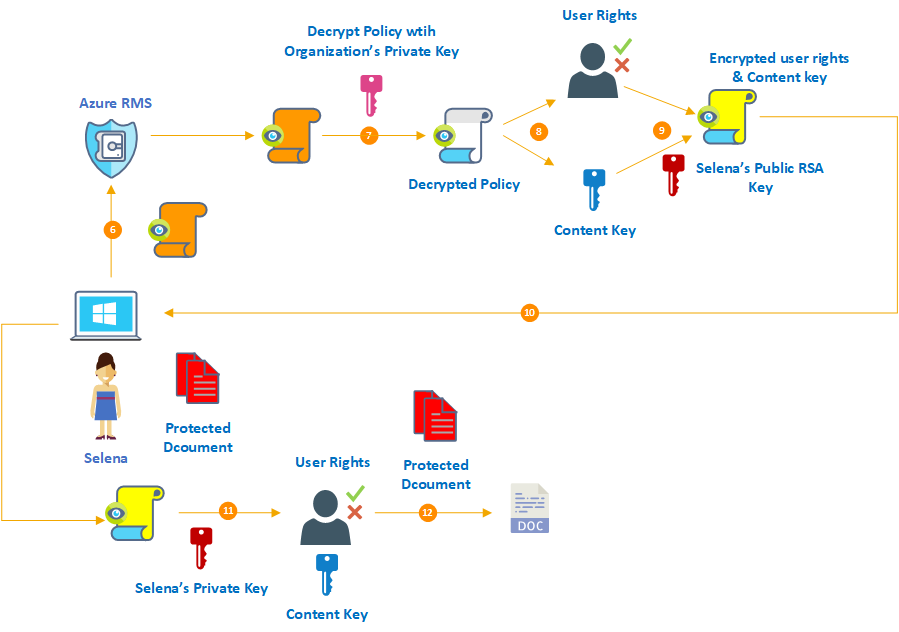
6. After Selena authenticates successfully, the system retrieve the policy and Andrew's certificate from the protected document and forwards it to Azure RMS.
7. Service decrypts the policy using the Organization's public key.
8. The decrypted policy contains Selena's access rights and content key. The system evaluates the permissions to understand the rights associated with the document.
9. In this step, content key re-encrypts using Selena's public RSA key. Then it is attached to user rights.
10. In this step, the above files are delivered to Selena's computer.
11. AIP client decrypts the user key and the content key using Selena's private key which was retrieved via initial user environment preparation process. This process reveals the user rights list and the content key.
12. With the help of the content key, the AIP client decrypts the encrypted document. AIP client also passes the right list to the application and it will decide what she can do with the document.
This completes the decryption process and at the end, Selena was able to open the protected document. The above scenario explains what is exactly happening behind the scene when we protect and consumer sensitive data using Azure RMS. I hope this was useful and If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.




very good and easy explanation.
but a little typo.
7. ‘private’ instead ‘public’