As we know, passwords are no longer strong. In Verizon Data Breach Investigations Report (2017), it says, 81% of hacking-related breaches used either stolen or weak passwords. Multi-factor authentication can provide an extra layer of security to the sign-in process but it doesn’t eliminate the requirement for passwords. In one of my previous blog posts, I explain how we can enable Azure Active Directory Password-less authentication by using FIDO2 Security keys. This required additional hardware components. Apart from that method now we also can use SMS to authenticate into Azure Active Directory. The beauty of this method is that you not even need to know your user name to log in. Your phone number will be your user name. This not only reduces the security risk; it also simplifies the complexity in the login process. This feature is still in public preview but it is not too early to test.
Prerequisites
To enable Azure Active Directory Password-less authentication with SMS , we must have the following,
1. Valid Azure Subscription
2. Azure AD Tenant
3. One of the following licenses assign to Azure AD user who going to use this feature,
• Azure AD Premium P1/P2
• Microsoft 365 (M365) F1/F3 or Office 365 F1/F3
• Enterprise Mobility + Security (EMS) E3/E5 or Microsoft 365 (M365) E3/E5
4. Global Administrator Account
Limitation
• SMS based authentication has the following limitations.
• This cant be used with native office applications (except teams)
• SMS based authentication is not compatible with Azure multi-factor authentication
• Can’t’ use with federation. Users only can authenticate in the cloud.
In this post I am going to demonstrate how we can enable SMS based authentication for Azure AD. In my demo setup, I have a user called Debra Berger (DebraB@M365x620957.OnMicrosoft.com). She is using Enterprise Mobility + Security E5 Licences. I am going to enable SMS-based authentication for her account.
Let’s go ahead and enable the SMS based authentication first.
1. Log in to Azure Portal (https://portal.azure.com/) as a Global Administrator
2. Click on Azure Active Directory tile.
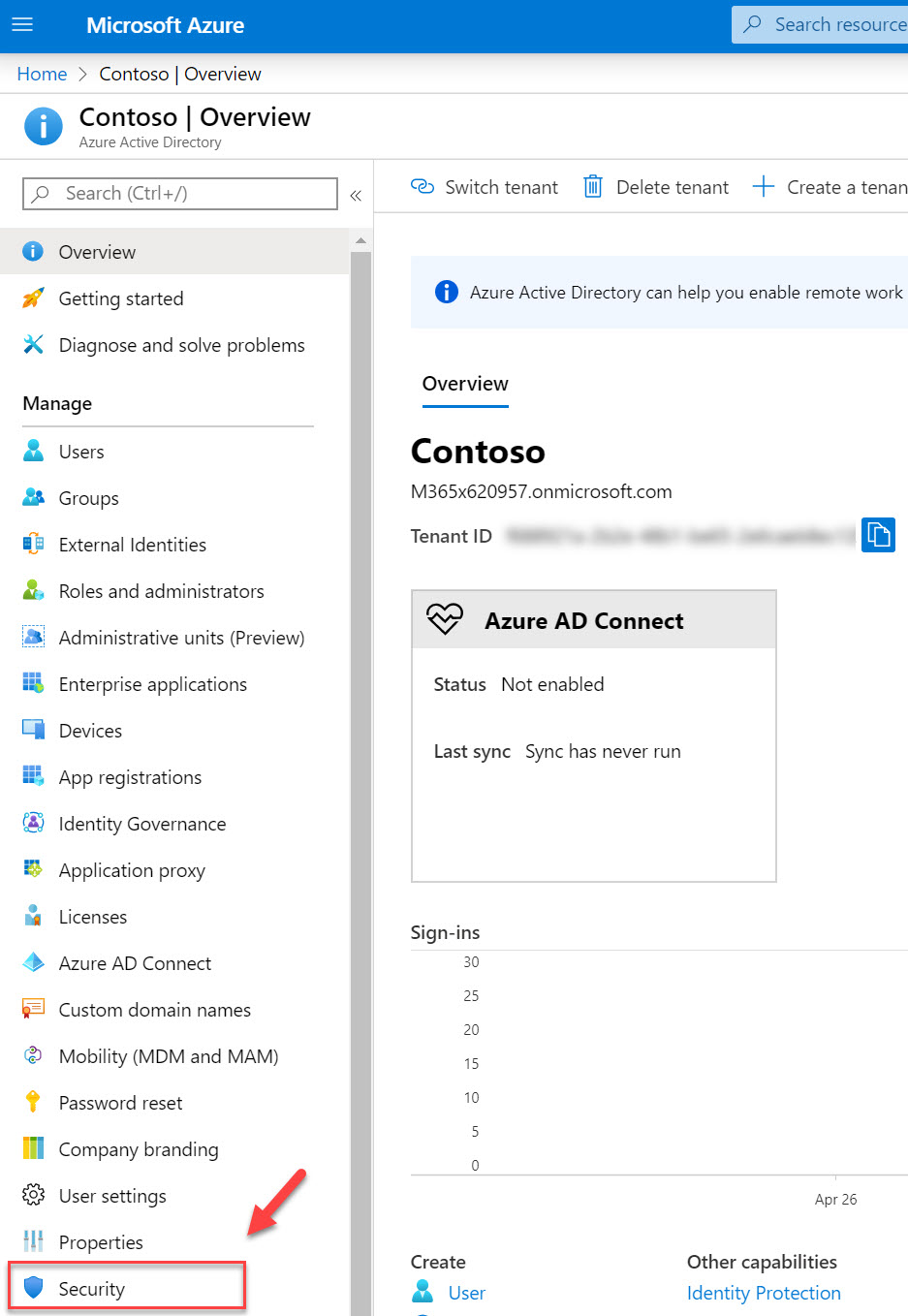
3. Then in the new window click on Security
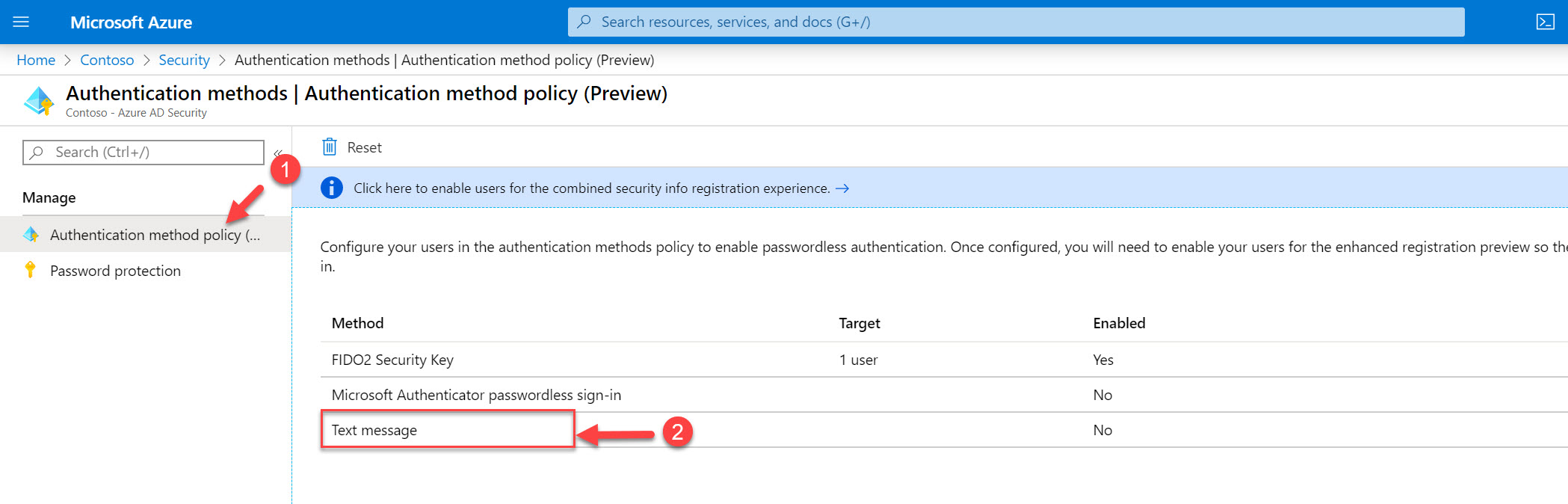
4. In the Security page, click on Authentication methods
5. Then click on the Authentication method policy (Preview) | Text messages
6. In the new window, click on Yes under ENABLE. Then click on Select users under TARGET. After, click on Add users and groups and select Debra Berger from the list. Leave all other settings in default and click on Save to apply the settings.
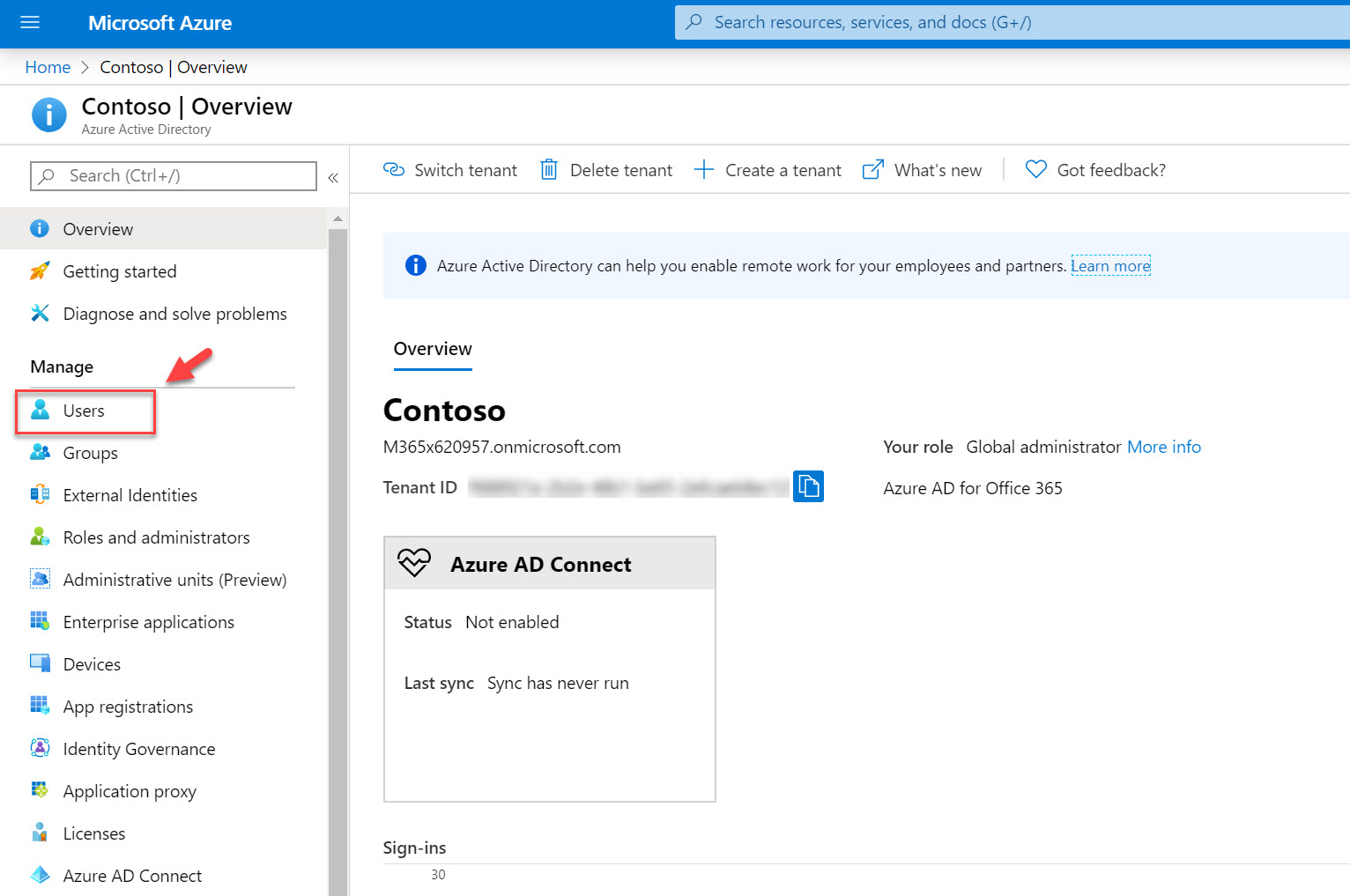
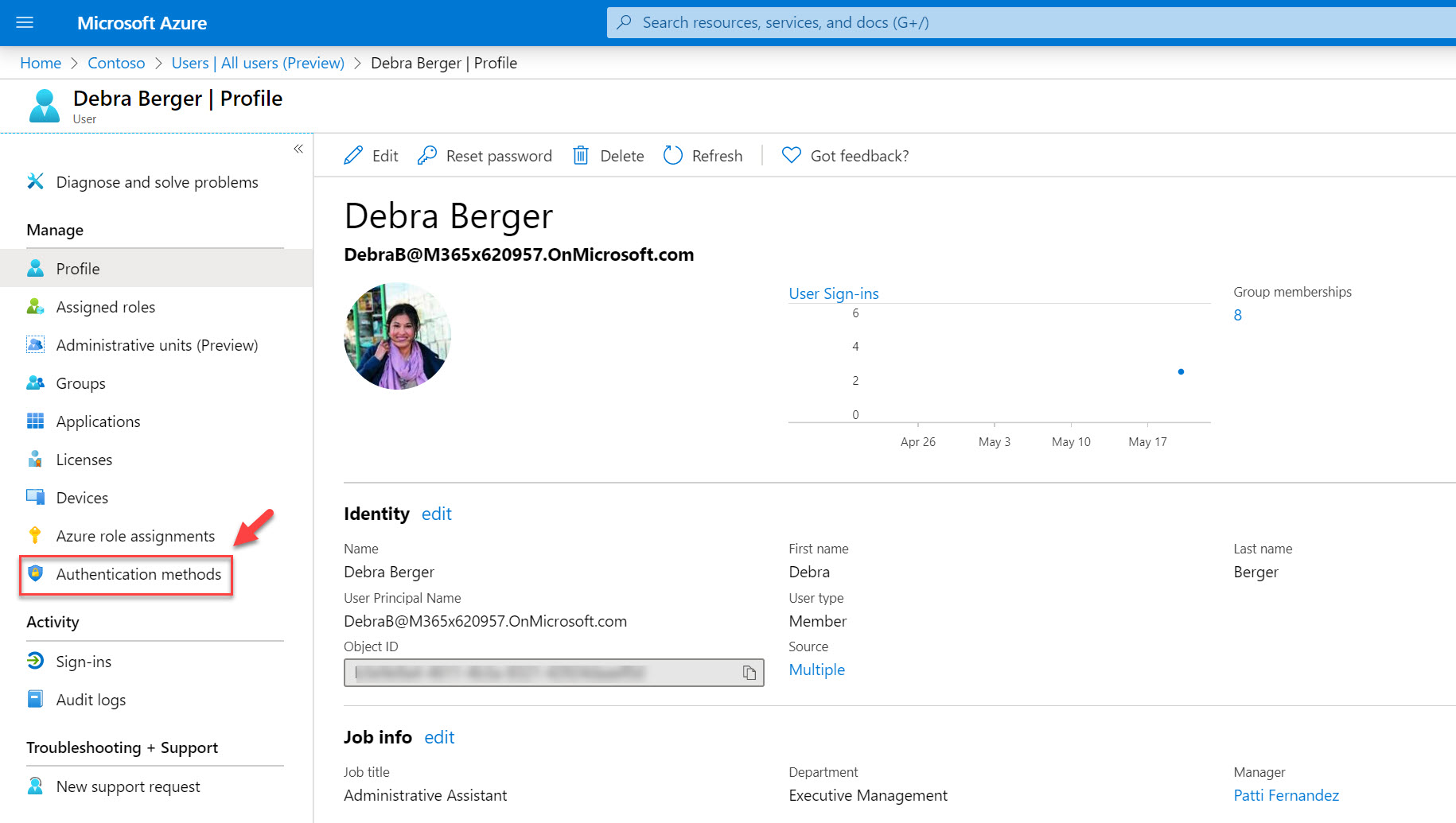
7. This completes the configuration of the service. The next step is to associate phone number data with user Debar. Users also can set this info by log in to My profile page. Go back to Azure AD home page and click on Users.
8. Search for the user Debra
9. In the profile page, click on Authentication methods
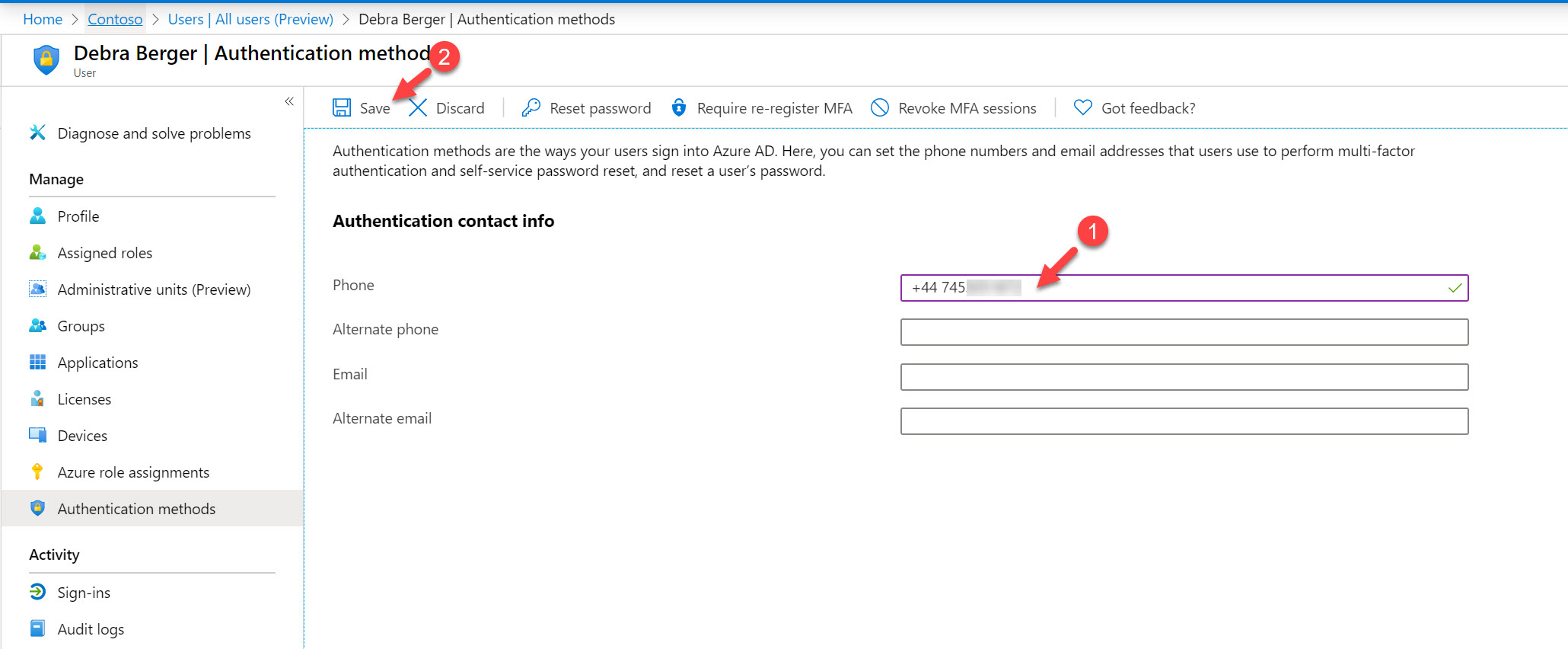
10. In the new window, type the phone number for the user including country code. Then click on Save to apply changes.
This completes the configuration process. Let’s go ahead and see this in action.
Password-less authentication Testing
To test SMS-based authentication,
1. Go to Office 365 Home page (https://office.com)
2. Click on the Sign In button.
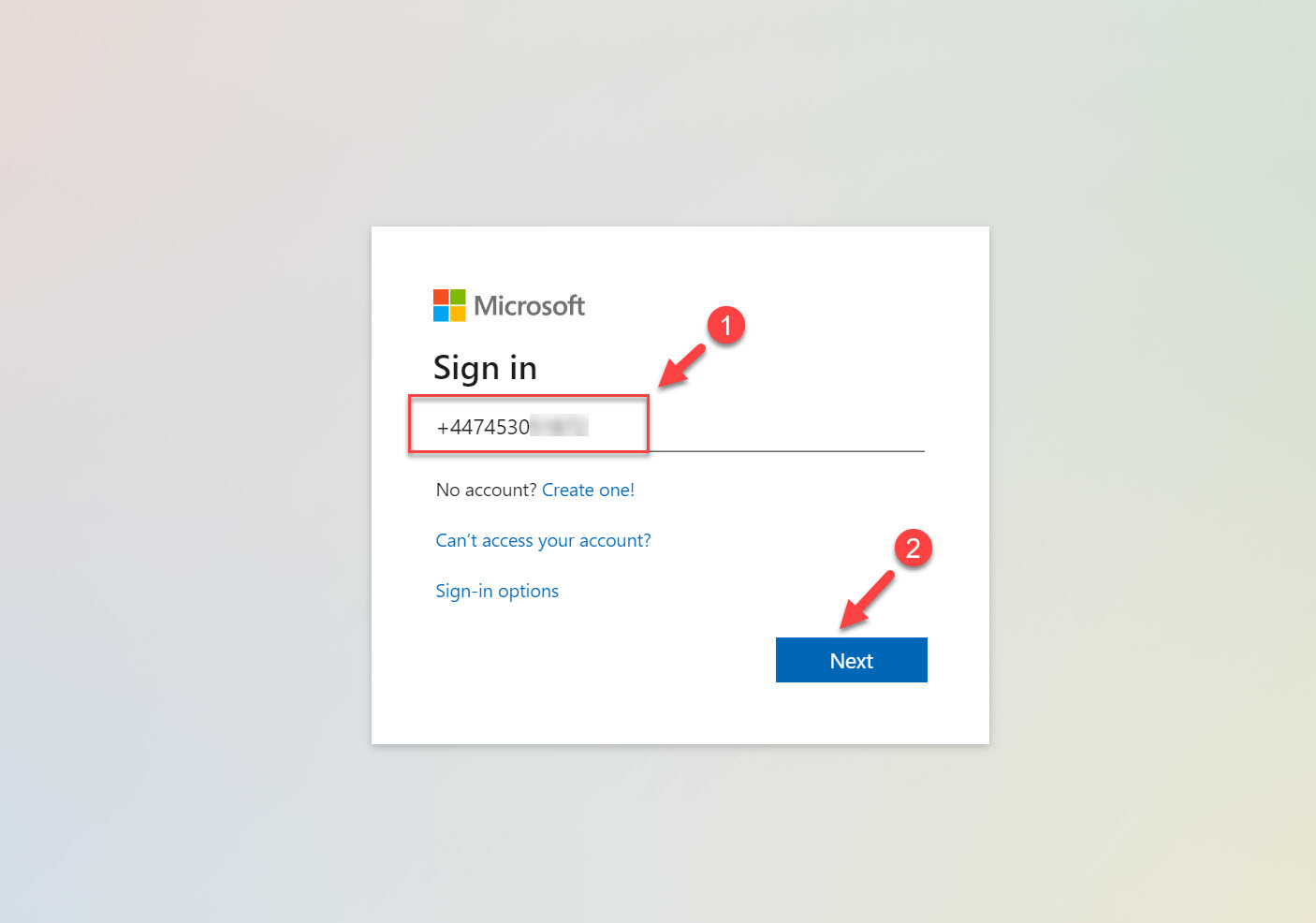
3. In Sign-in box, type the phone number for the user name field and click on Next
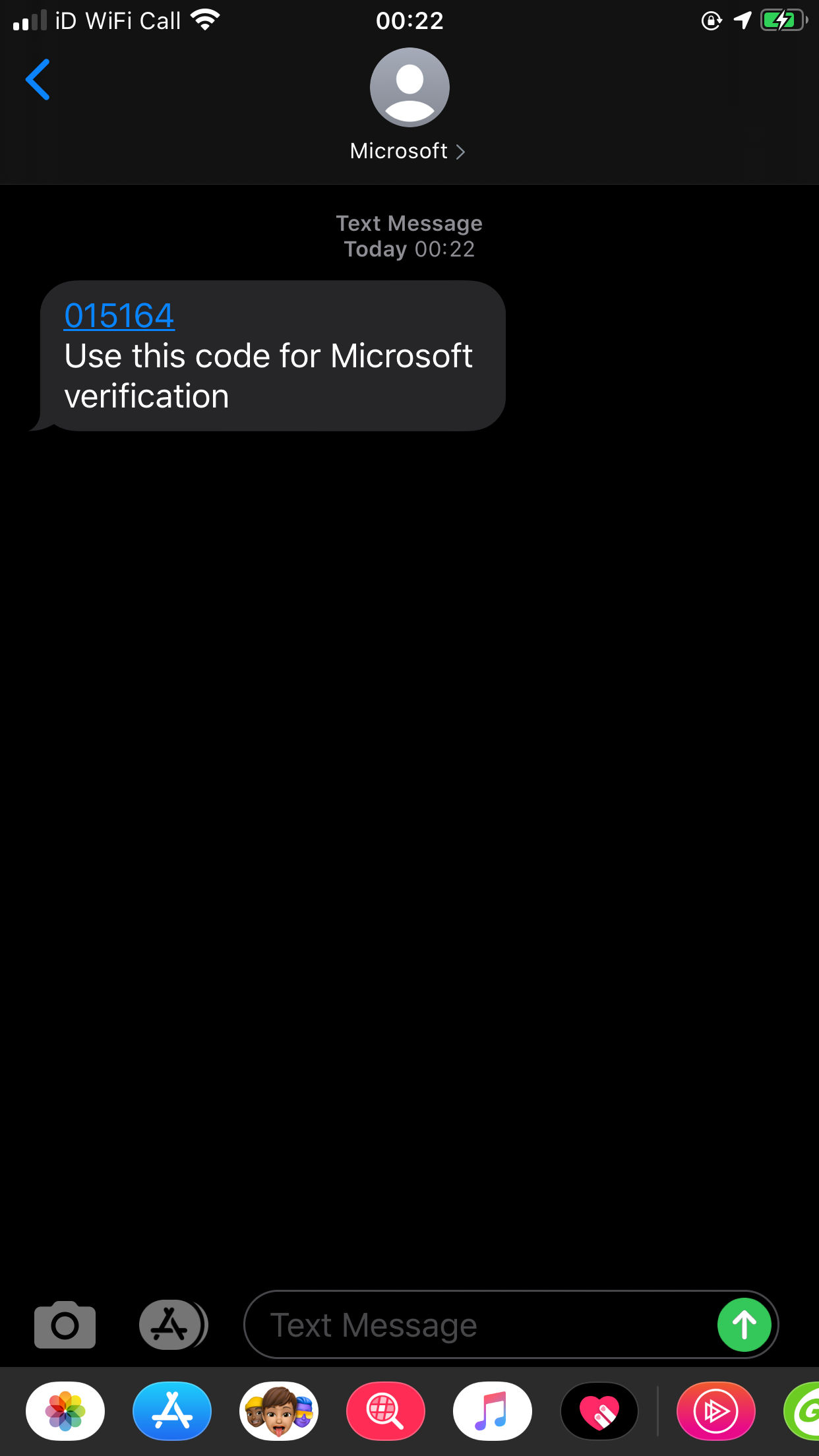
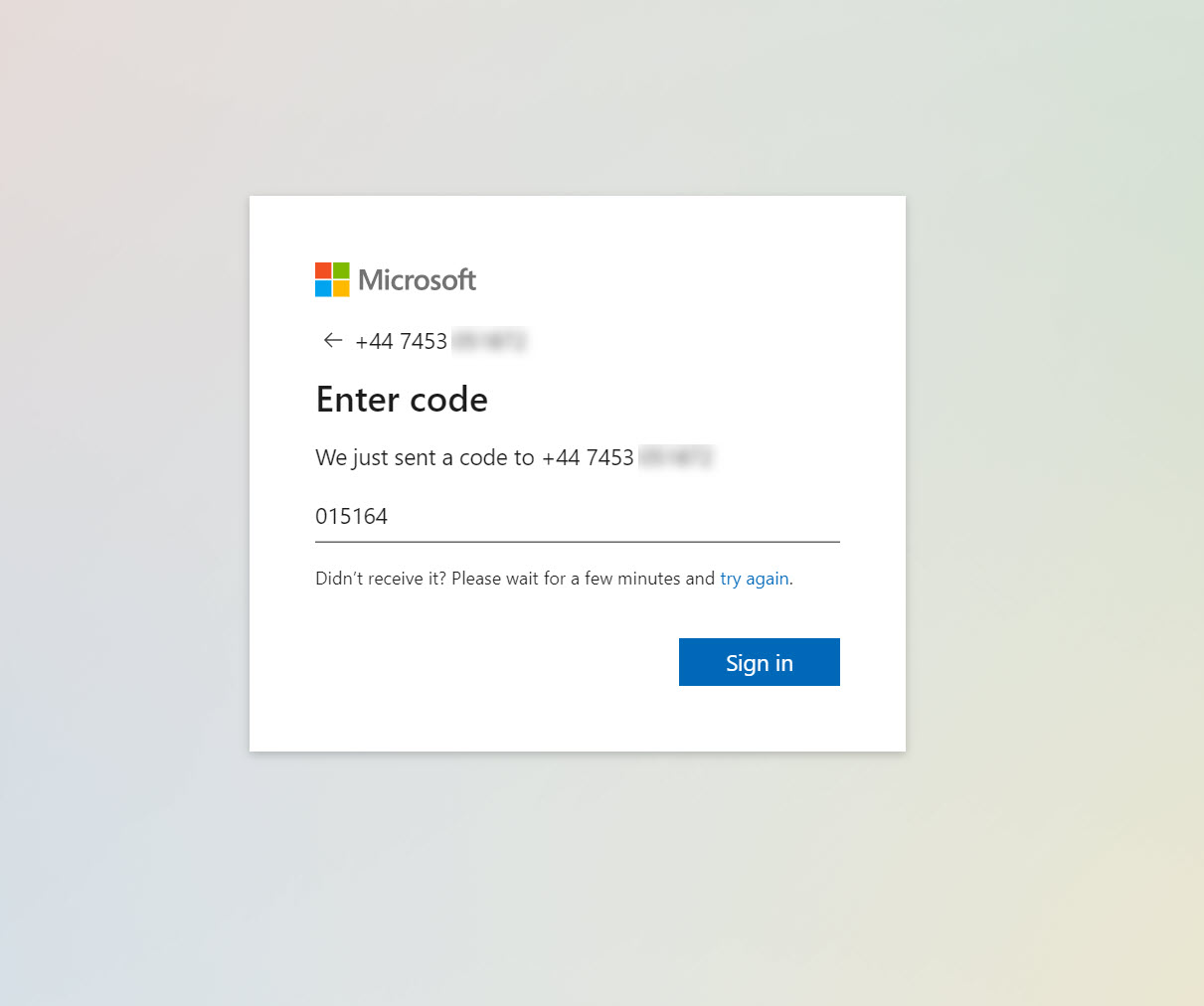
4. This will send SMS message with OTP code.
5. Type the code and click on Sign in to complete the authentication process.
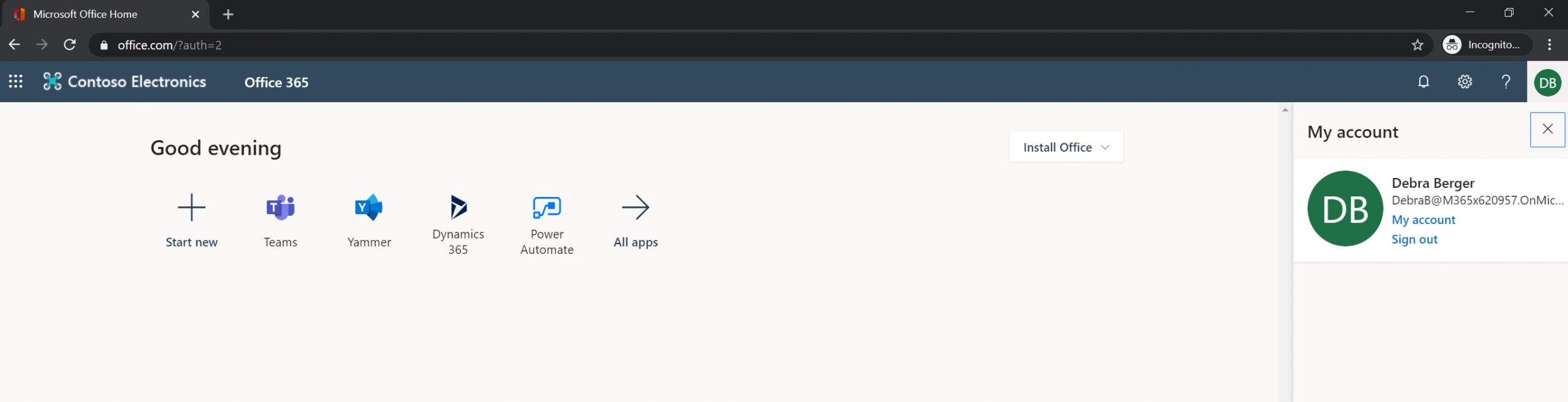
6. As expected, user Debra can access the office portal successfully. Nice and simple!
As we can see above, Password-less authentication is working with SMS as expected.
This marks the end of this blog post. If you have any further questions about this feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.