Group Policy can map to Sites, Domain and OUs. If group policy is mapped to OU, by default it will apply to any object under it. But within a OU, Domain or Site there are lots of objects. The security, system or application settings requirements covers by group policies not always applies to boarder target groups. Group Policy filtering capabilities allows to further narrow down the group policy target to security groups or individual objects.
There are few different ways we can do the filtering in group policy.
1) Security Filtering
2) WMI Filtering
In this post we are going to look in to Security Filtering. In one of my previous post I already covered WMI filtering. It can be found under http://www.rebeladmin.com/2018/02/group-policy-wmi-filters-nutshell/
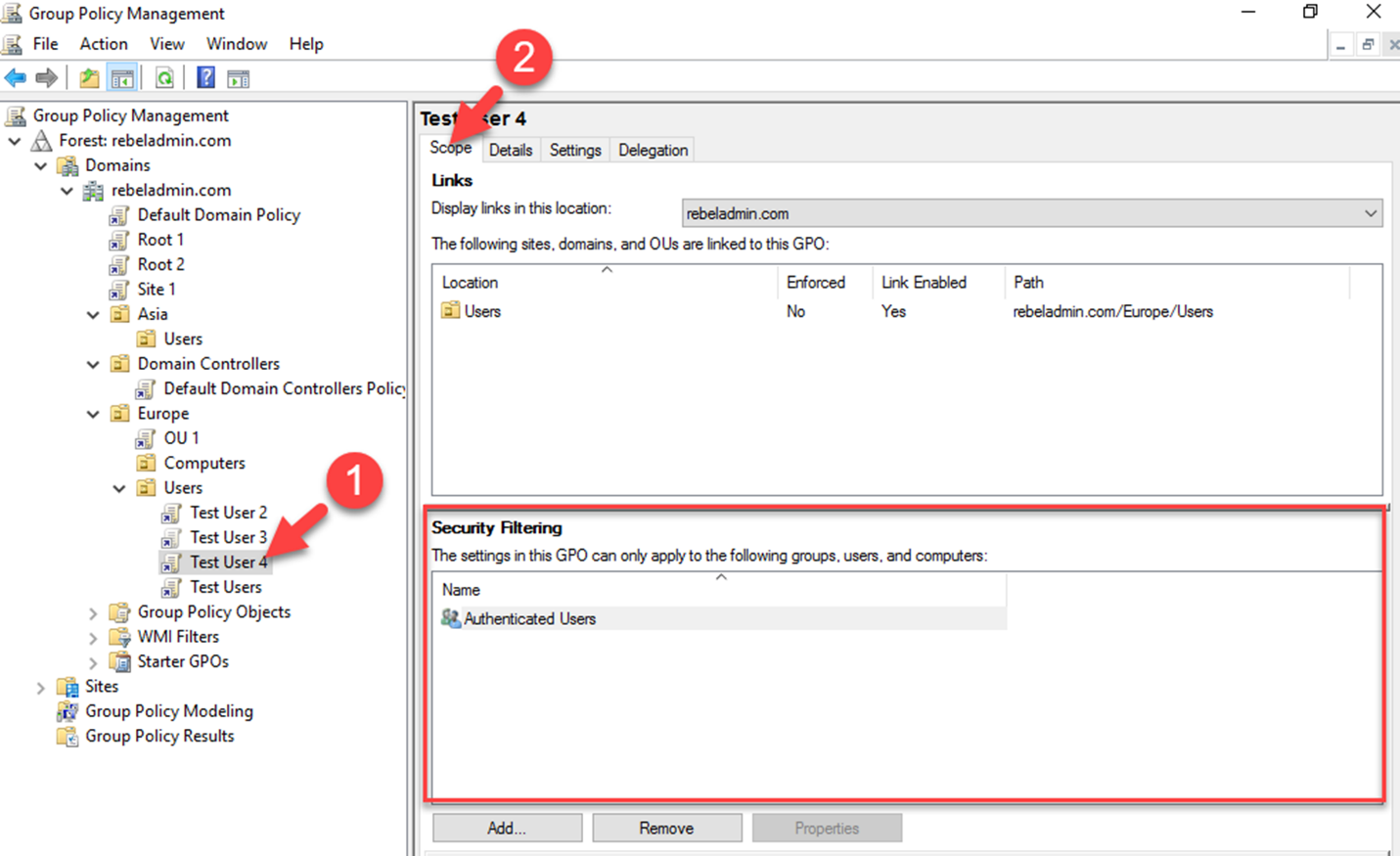
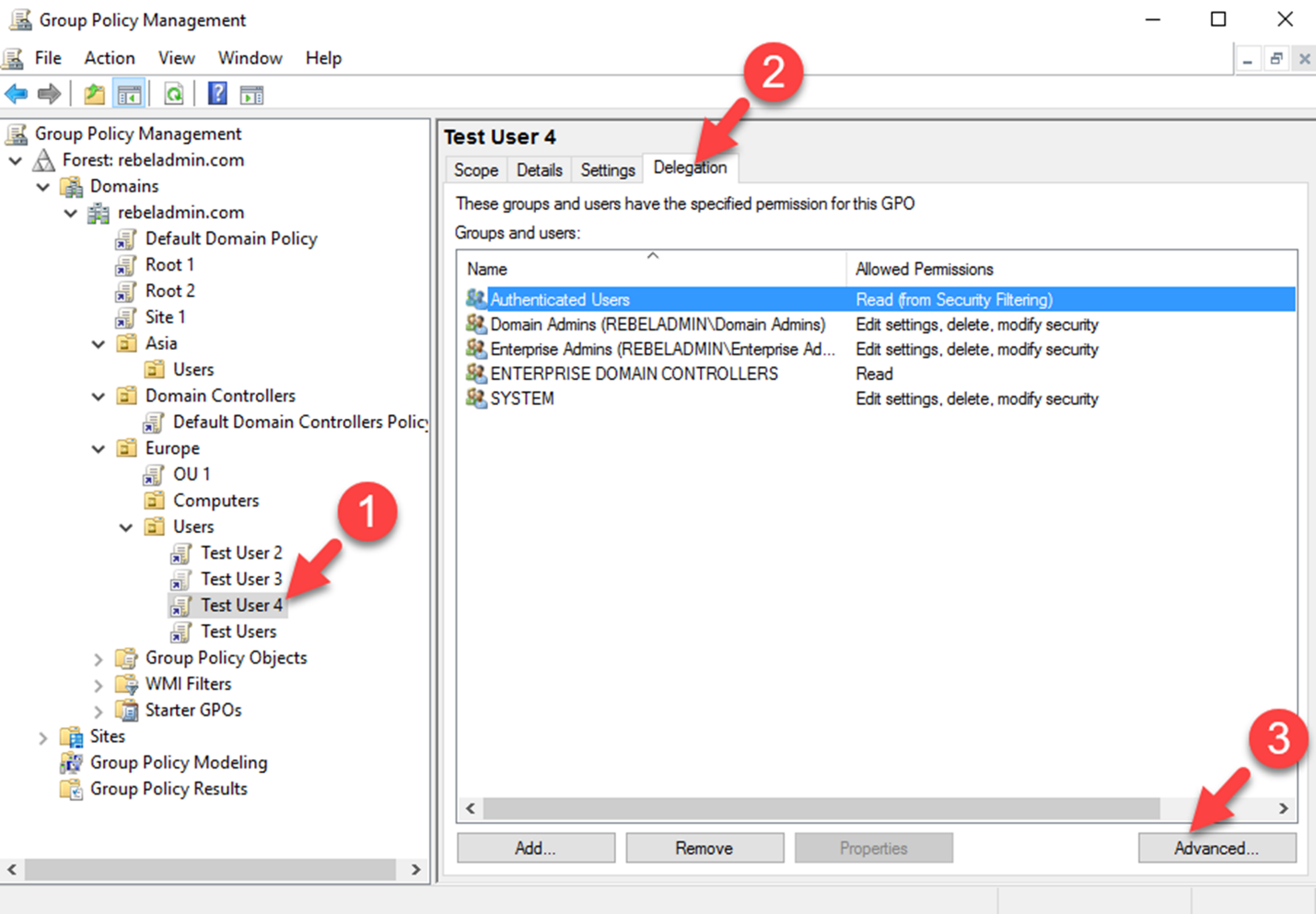
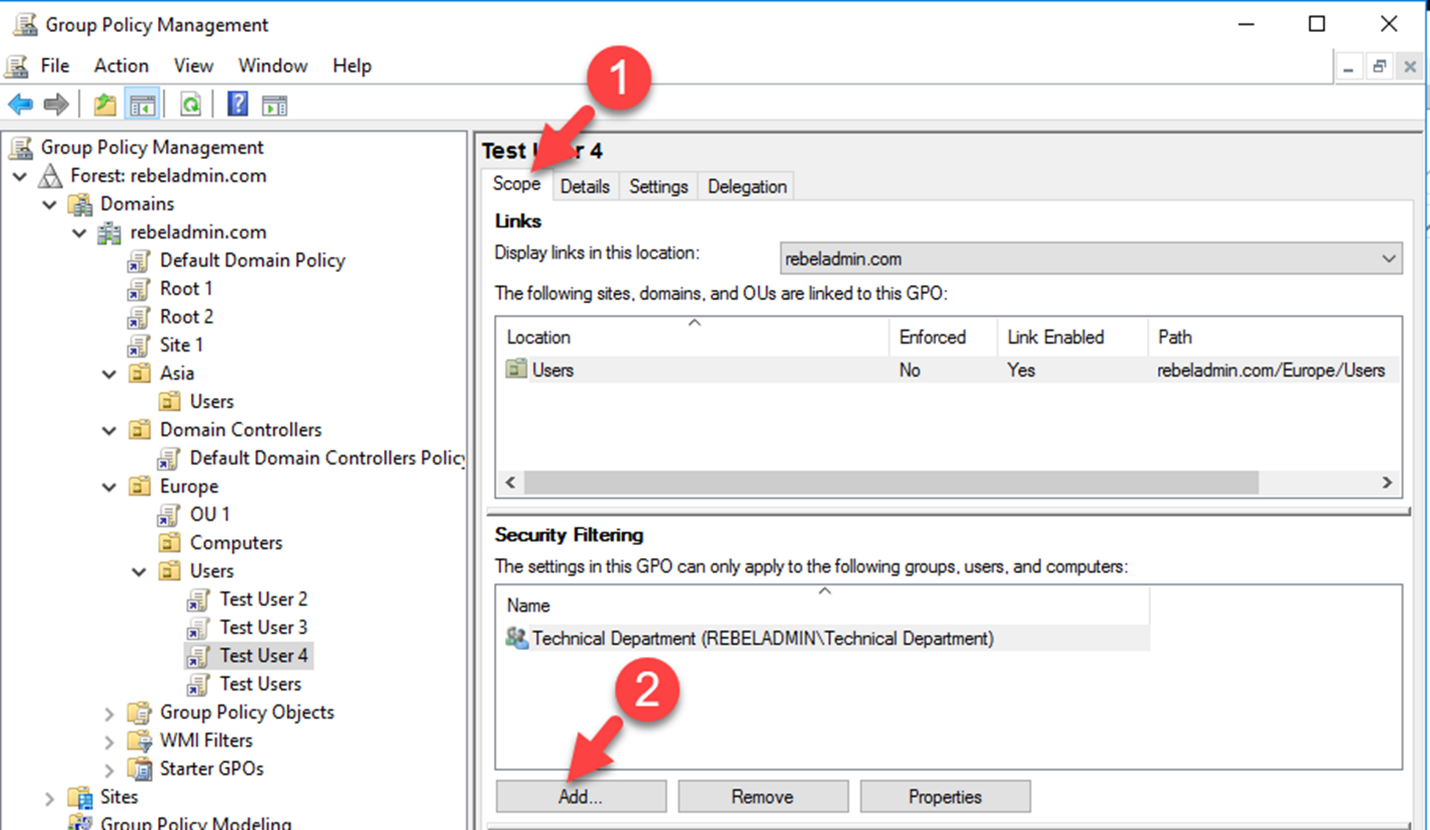
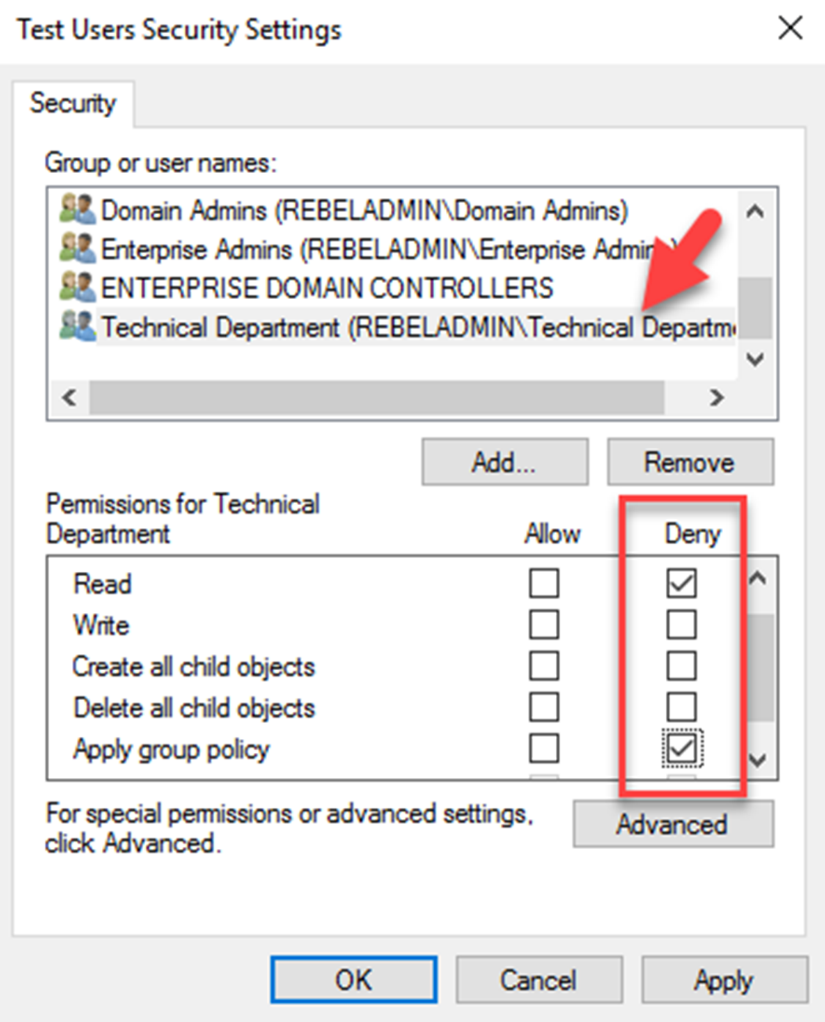
Before apply the security filtering, the first thing to make sure is group policy mapped correctly to the Site, Domain or OU. The security group or the objects you going to target should be under correct level where group policy is mapped.
We can use the GMPC or PowerShell cmdlets to add the security filtering to GPO.



Well explained . Wonder why no comments so far?
You save my day! Uncheck “Apply group policy” to authenticated group works like a charm.
This is a very nice explanation and thanks to you for your time and effort as well.
Great Article. Well explained and helpful, Thanks !
thank you! You helped me a lot
Awesome, the content and the explanation is perfect, helped me a lot
You are a genious Mr. Dishan Francis. It worked for me as expected.
Dishan:-
A much needed light.
Thank you for sharing graciously and concisely.