In part 01 of this series we learned RMS and its capabilities. if you didn’t read it yet, you can find it in here. In part 02 we learned about AD RMS components. You can read it using
In part 03, I am going to explain how AD RMS works.
By now we know the components of the AD RMS and its capabilities. In this section, we are going to look in details to understand how all these components work together to protect corporate data.
Before start the data protecting process, we need to have healthy AD RMS Cluster, AD RMS Clients (Author and Recipient) and reliable connection between those components. Once these prerequires fulfill, Data protection process will happen in three main stages which is protect content by author, publish protected content and access protected content by recipient. Let’s assume Peter is trying to protect a document using AD RMS. He going to send it to Adam and he do not want him to edit or print it. This is the first time he going to use AD RMS. In AD RMS environment, user Peter will refer as Information Author. On his first authentication in to AD RMS cluster, it creates Right Account Certificate (RAC) and it will be user’s identity in AD RMS. This is a onetime process. This certificate contains the public key and private key of the Peter which is encrypted by his computer’s public key. When Peter register with AD RMS cluster it also creates another certificate called Client Licensor Certificate (CLC). This CLC includes Client Licensor Certificate’s public key and private key which is protected by public key of Peter. It also includes AD RMS cluster public key which is signed by AD RMS private key.
Peter decides what data need to be protected first. Then it generates symmetric key (random) and encrypt the data which needs to be protected. It uses AES-256 standards to encrypt the data. When first AD RMS server added to the cluster, it creates another certificate called Server Licensor Certificate (SLC). This represent the identity element of the AD RMS server. This is shared with clients so they can use to exchange confidential data in secure way. SLC includes the public key of the AD RMS server. As the next step the system will encrypt the symmetric key used for data encryption by using it. So, only AD RMS cluster can open it.
After that RMS Client creates Publishing License (PL). This PL use to indicate allowed recipients, what rights they got and what condition will apply towards protected data. PL includes encrypted symmetric key that can used to decrypt the protected data. All these data then encrypt with Server Licensor Certificate’s public key. Apart from that AD RMS client also will sign encrypted data with private key of CLS. At the end this protected data will attached to PL. it also included the copy of symmetric key which is encrypted with CLS public key. This confirms Peter’s authority over the protected document, so he can decrypt the document without using another license. Once all these encryptions and signings are done, the document is ready to send over to Adam.
Once Adam receives the document, his Ad RMS aware application try to open it and found it is a protected document. Similar to Peter, Adam already have his RAC and CLS from the AD RMS Cluster. In order to open the protected document at once does it encrypt it with does it encrypt or sign with any of Adam’s certificates? No, it’s not. But his AD RMS client knows who need to contact in order to sort it out for him. To open the protected document Adam should have a Use License (UL). This is issue by the RMS cluster. So, AD RMS client request for license also included encrypted Publishing License, Encrypted Symmetric Key, Peter’s CLC and Public key of Adam’s RAC. The protected document will not send over with this request to RMS Cluster. To decrypt the protected document Adam needs the Symmetric key which used by Peter to encrypt the document. As first step Server needs to know if Adam is permitted to access the document, if he is permitted what sort of conditions and rights will apply. This info is in Publishing License. It is encrypted using public key of SLC. AD RMS server is the private key owner for it and he can easily extract it. if Adam is not allowed in PL, it will be declined the access to it. if its allowed it creates a list mentioning Adam’s rights to the document. The most important part of the decryption process is to retrieve the Symmetric Key. This is also encrypted by SLC’s public key. Once it is extract, it will be re-encrypt using Adam’s RAC public key. it was a part of the Use License request. This ensure, the only one can see the key is Adam’s system. Since server got all the required information, it generates Use License including the permission list and encrypted symmetric key. then it sends over to Adam’s RMS client. Once it reaches Adam’s system, it can decrypt the symmetric key using RAC’s private key. then RMS aware application will decrypt the document and attach the rights information retrieved from the User License. At the end, voila!!! Adam can see the content of the document.
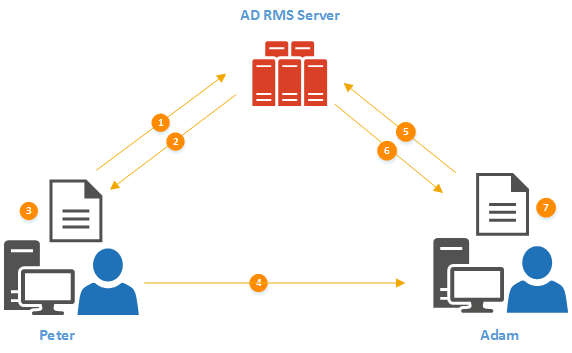
In above I have talked lots about different certificates, licenses, data encryption and decryption. I thought its still better to explain it in high level to recap things we learned.
Peter wants to send protected document to Adam. Adam should only have read permission to the document and should not be able to modify or print.
1) This is the first-time peter going to use AD RMS. As soon as he tries to protect the document, RMS client initiate a connection to AD RMS server (cluster)
2) AD RMS Server replied with Right Account Certificate and Client Licensor Certificate. This is one time process.
3) In Peter’s system, random symmetric key is generated and encrypt the document using it. Then this symmetric key is encrypt using SLC’s public key. After that it is attached to a Publishing License which includes Adam’s rights for the protected document. After that PL attached to encrypted document.
4) Peter sends protected document (along with this additional info) to Adam.
5) Adam’s RMS Aware application try to open it and found that it need Use License from AD RMS Server. then RMS client request it from the RMS Server.
6) RMS server decrypt the symmetric key and the PL. after that server checks if the requester match with the PL. in our scenario it matches, so it went ahead and creates Use License. This includes symmetric key (it re-encrypts using Adam’s RAC Public Key) and a list which contains rights describes in PL. Then it delivers to Adam’s system.
7) Once Adam’s system receives the Use License, it retrieves Symmetric key and decrypt the document. Then Adam open the document and use it according to rights described on PL.
This marks the end of this blog post. In Part 04, I will demonstrate deployment of AD RMS. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.