In my last 2 posts I explain about Restricted RDP and Protected User Group features available in windows 2012 R2 directory service to protect your high-privileged accounts. Authentication Policies and Authentication Policy Silos also a feature available for windows server 2012 R2 directory services to protect your AD infrastructure’s high privileged accounts.
Let me explain in simple terms, in my network I have exchange mail server running. I got exchange administrator. We also got a “Management PC” which uses for the administration tasks. So for fact I know the exchange administrator account should only use either in exchange servers, management pc. If this account is log in to receptionist’s pc there is something wrong. It can be possible security breach. So what if I can limit this exchange administrator access only to exchange servers and management pc? Also what if I can apply more security for account authentication to protect this high privileged account? Yes Authentication Policies and Authentication Policy Silos is for that.
Authentication policy defines the Kerberos protocol ticket-granting ticket (TGT) lifetime properties and authentication access control conditions for an account type.
Authentication policies control the following:
• The TGT lifetime for the account, which is set to be non-renewable.
• The criteria that device accounts need to meet to sign in with a password or a certificate.
• The criteria that users and devices need to meet to authenticate to services running as part of the account.
Authentication policy silos are containers to which administrators can assign user accounts, computer accounts, and service accounts. Sets of accounts can then be managed by the authentication policies that have been applied to that container. This reduces the need for the administrator to track access to resources for individual accounts, and helps prevent malicious users from accessing other resources through credential theft. (https://technet.microsoft.com/en-GB/library/dn486813.aspx)
In order to use this, we need to have minimum of windows 2012 R2 domain functional level running. Also need to have Dynamic Access Control Support.
Enable Dynamic Access Control for DC
Let’s see how we can enable DAC support.
1) Log in to DC as domain or enterprise administrator
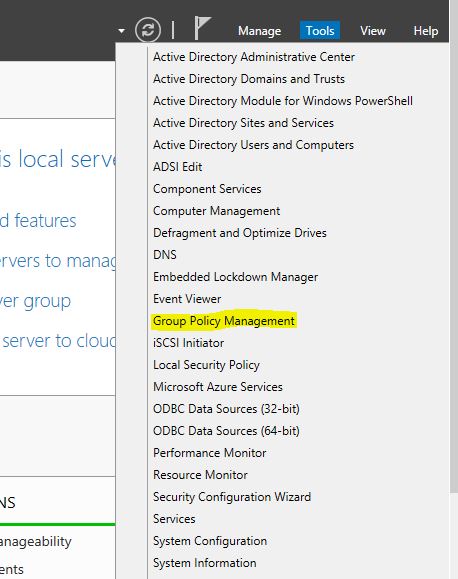
2) Server Manager > Group Policy Management
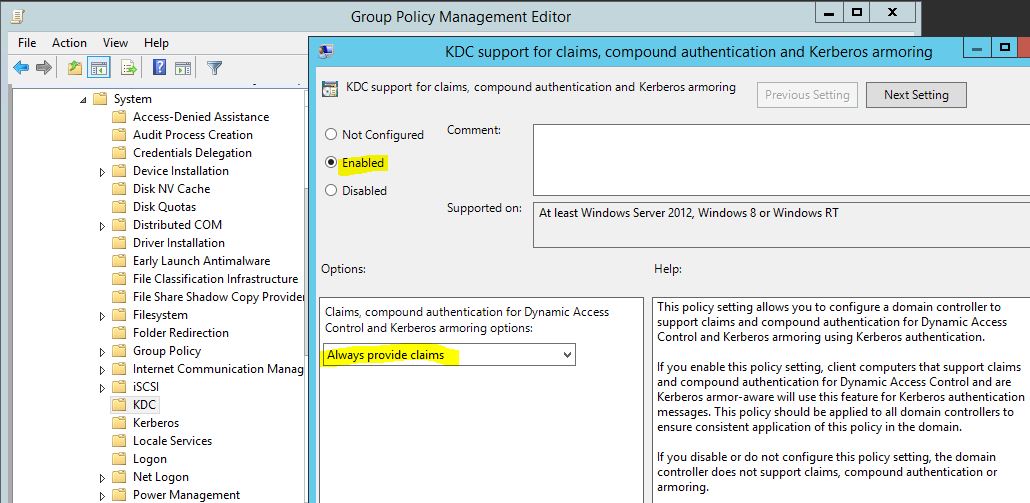
3) Then Create New GPO, go to Computer Configuration > Administrative Templates > System > KDC, then set it to enable and option to always provide claims
Enable Dynamic Access Control for Hosts and Devices
1) Log in to DC as domain or enterprise administrator
2) Server Manager > Group Policy Management
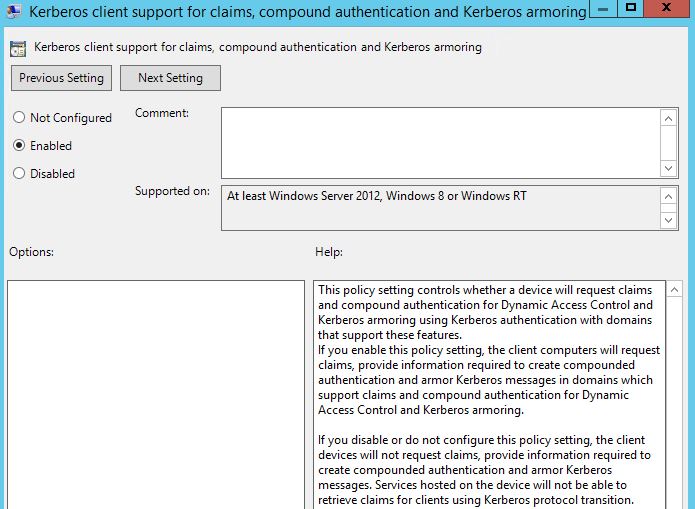
3) Then Create New GPO, go to Computer Configuration > Administrative Templates > System > Kerberos, then set it to enable
This policy setting allows you to configure a domain controller to support claims and compound authentication for Dynamic Access Control and Kerberos armoring using Kerberos authentication.
Create Authentication Policy
1) Log in to DC as domain or enterprise administrator
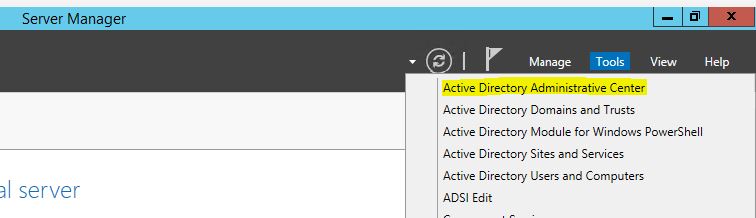
2) Go to Server Manager > Active Directory Administrative center
3) Then go to “Authentication”
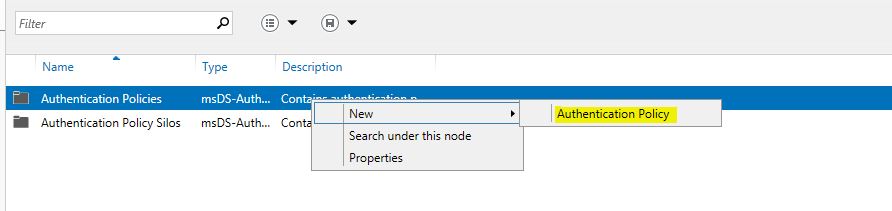
4) Right click on Authentication policy > New > Authentication Policy
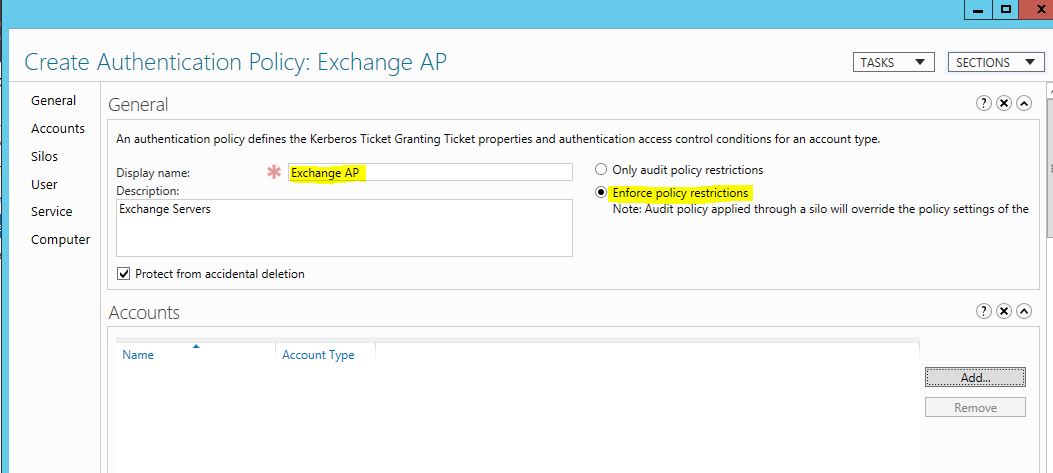
5) Then in New Wizard opens. Provide name and Description for it. Also click on “Enforce Policy Restrictions”
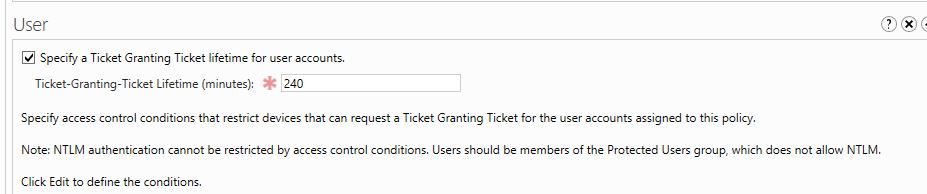
6) Then Under the “User” section define the number of minutes for the TGTL. For this policy I am going to use 4 hours TGTL.
7) Then click ok to create the New Policy
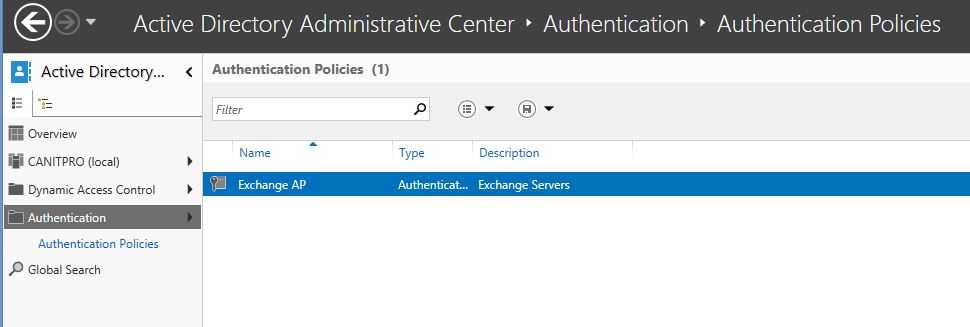
8) Now You can see New Policy is Created
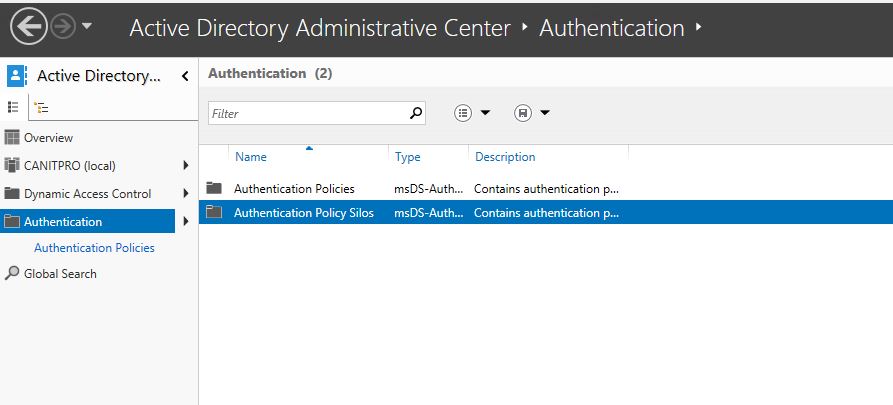
Create Authentication Policy Silos
To create Policy Silos
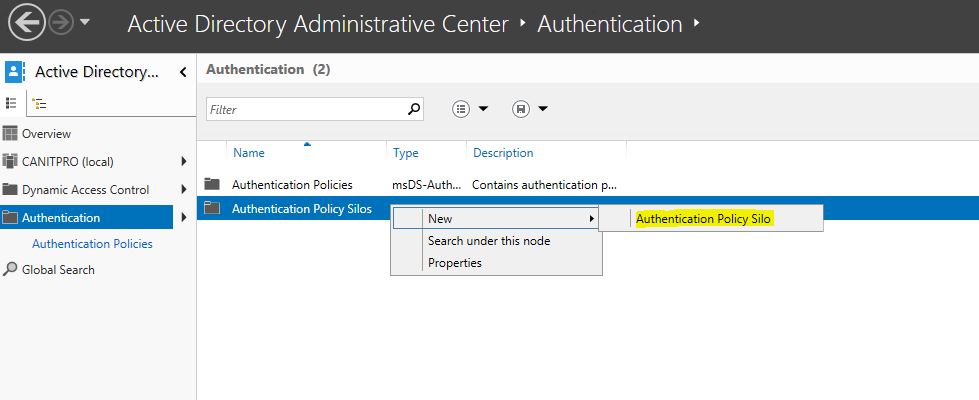
1) Server Manager > Active Directory Administrative center > Authentication Policy Silos
2) Right Click > New > Authentication Policy Silo
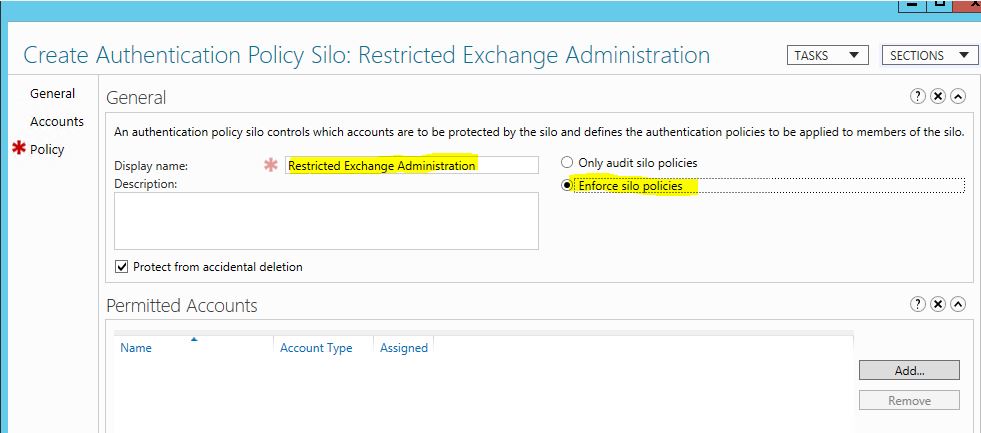
9) Then in new wizard, provide name for policy silo, in my demo I used “Restricted Exchange Administration” then also select “Enforce Policy Restrictions”
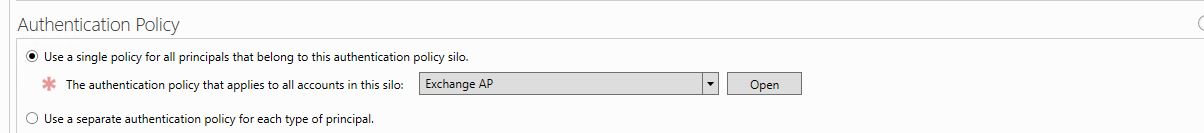
3) Under the authentication policy section select Use a single policy for all principals that belong to this authentication policy. Then from drop down select the authentication policy created in previous section.
4) Click on ok to create the policy silo
Assign Policy Silos
Next step is assign this policy silos to objects
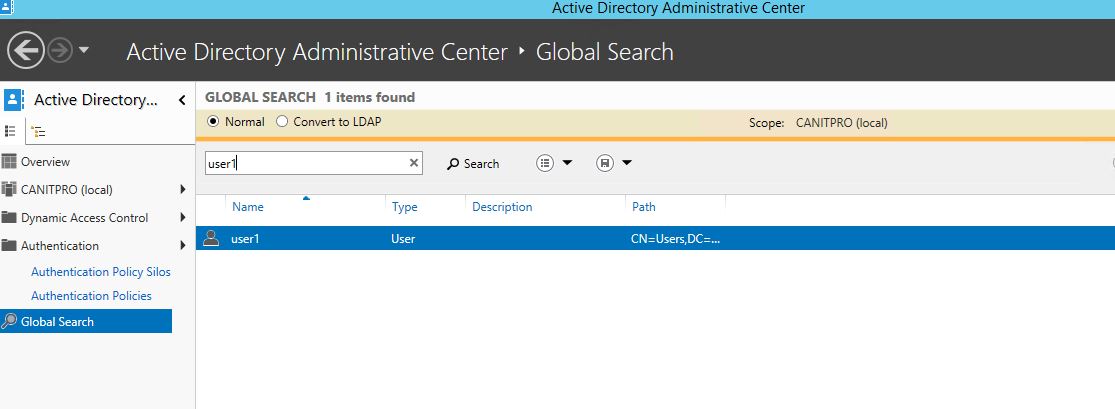
1) In ADAC, go to global search and search for the object
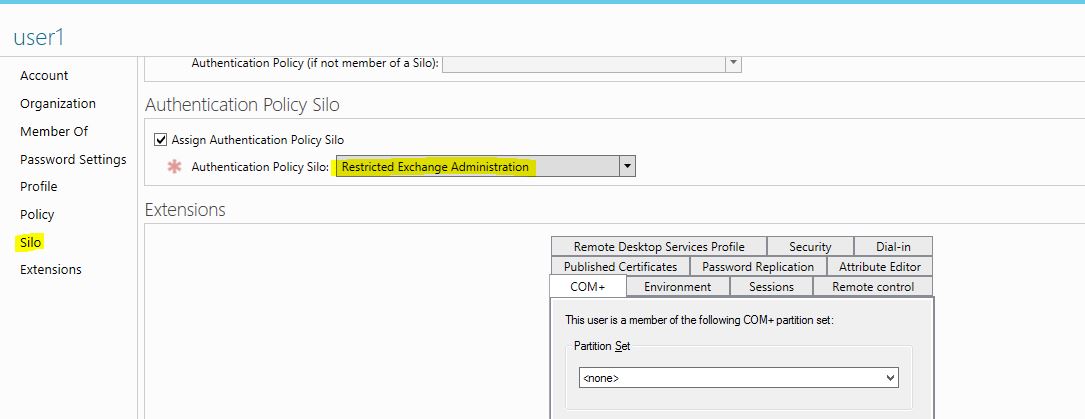
2) Double click on object. Once its open the property window go to silos option
3) In their select the new policy silo created and click ok
4) This can be computer object, user accounts
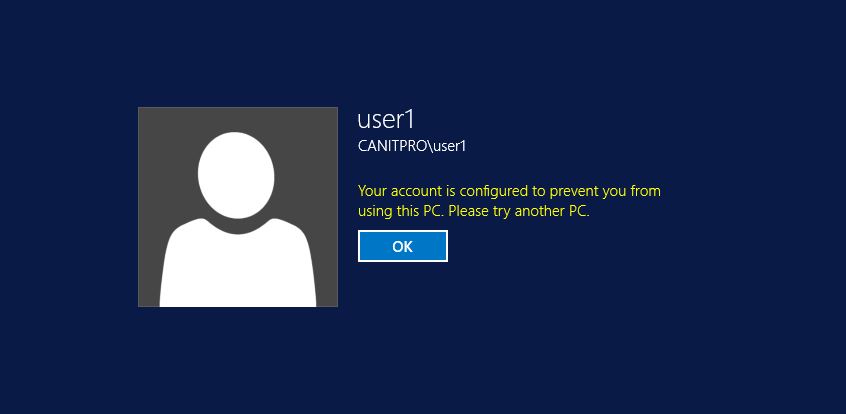
In here in my demo I wanted to protect user1 by login in to pc called DCPM01.
Once this rules applied, when I try to log in to the DCPM01 with user1 I get,
Hope you get idea about use of authentication policies and policy silos.
If you have any questions feel free to contact me on rebeladm@live.com



Wow !! Well Explained !! Thank you for your contribution !!