Today’s rapidly changing digital landscape creates new identity and access challenges. Microsoft Entra product family is capable of addressing these new challenges by securing identities, verifying identities, managing the life cycle of identities, enforcing least-privilege access, unified administration, and simplifying the access experience.
Microsoft Entra Permissions Management is part of the Entra family and it is a cloud infrastructure entitlement management (CIEM) solution. It can discover permission risks, automatically right-size permissions, and then continuously monitor the permission usage to detect anomalies. This is not only for Azure resources and Microsoft Entra Permissions Management also works with Amazon Web Services (AWS), and Google Cloud Platform (GCP).
Based on the roles, and responsibilities we are assigning different permissions to users or resources. Studies show over 90% of these identities only use less than 5% of the permissions they have. This Permissions Gap also has an impact on the risk of breach. When this gap is increased risk of the breach also increased as it creates more room for permission misuse (accidental or breach). Permission Creep Index (PCI) in Microsoft Entra Permissions Management gives granular visibility into actions performed by every identity on every resource. It generates a single metric value which helps to identify the Permissions Gap. If the score is higher it means there are a higher number of unused permissions in the environment. After this initial discovery phase, we will have a better understanding of the risks we need to focus on.
Microsoft Entra Permissions Management allows remediating the permission risks based on policies that enforce lease privileges and Just-in-Time (JIT) access. This will ensure identities have enough permissions to do their task in the given period of time. The ultimate goal is to reduce the Permission Gap.
Even though we have policies and control in place, It is important to keep eye on potential vulnerabilities in the environment. As we know risks related to identities are continuously developing in the cloud world. Microsoft Entra Permissions Management is capable of machine learning-powered (ML-powered) anomaly detection. It can provide context-rich forensic alerts and reports which can support rapid investigation and remediation.
In this first part of the blog series, I am going to demonstrate how to enable Permissions Management in your organization by onboarding Azure Subscription. We also can onboard AWS and GCP but that will cover in a later blog post.
Prerequisites
Before starting make sure you have the following,
1) Global Administrator Account – To enable Permission management we required a global administrator account in the Azure AD tenant.
2) License – Microsoft Entra Permission Management required paid license and it can purchase via https://aka.ms/BuyPermissionsManagement . However, we can start with 45-days free trial https://aka.ms/TryPermissionsManagement
3) Azure CLI or PowerShell – We are required to run certain commands during the onboarding process. You can install Azure CLI by following the steps in here https://learn.microsoft.com/en-us/cli/azure/install-azure-cli-windows?tabs=azure-cli
4) Permission – For the onboarding process we need at least Microsoft.Authorization/roleAssignments/write permission
Microsoft Entra Permissions Management Configuration
Once the above prerequisites are in place,
1) Log in to Entra portal https://entra.microsoft.com/
2) Click on Permission Management
3) If it’s the first time, make sure to apply for the relevant licenses.
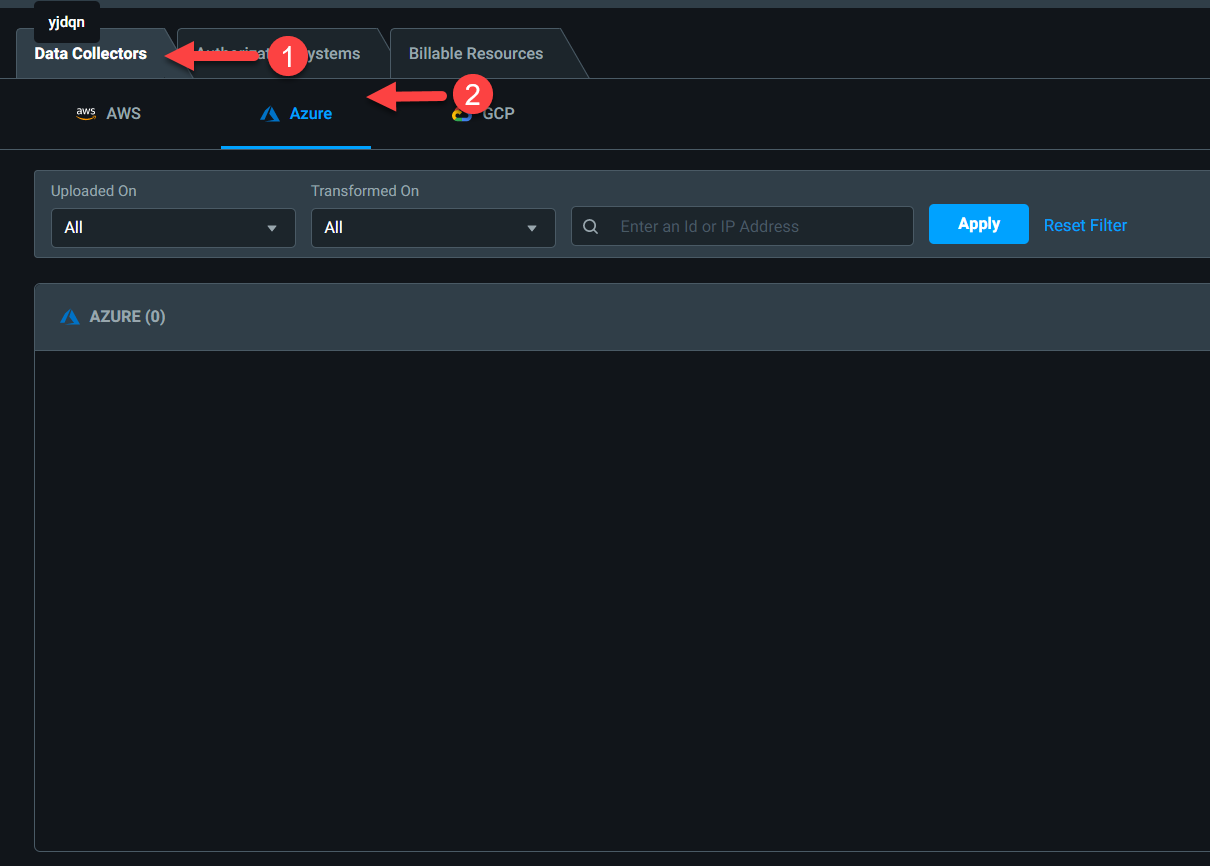
4) Then on the new page, click on Data Collectors | Azure
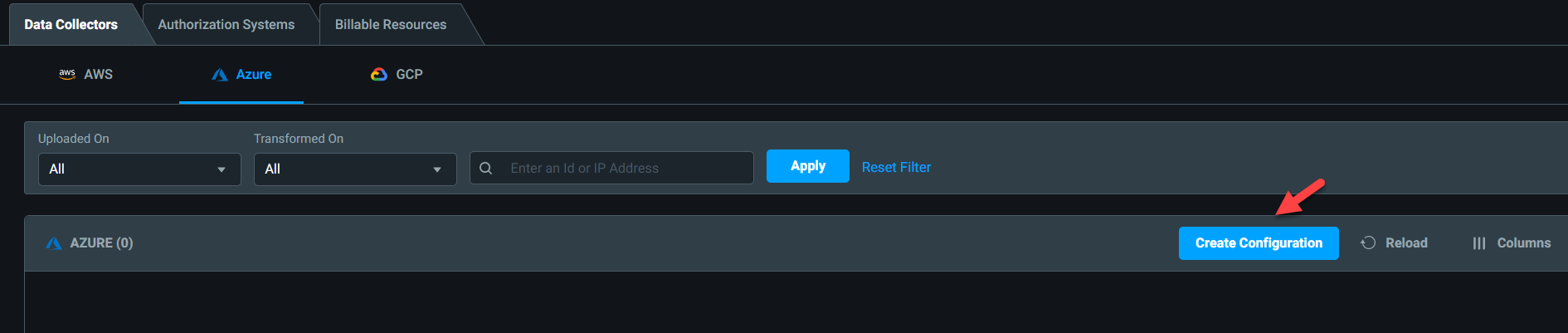
5) Next, Click on Create Configuration
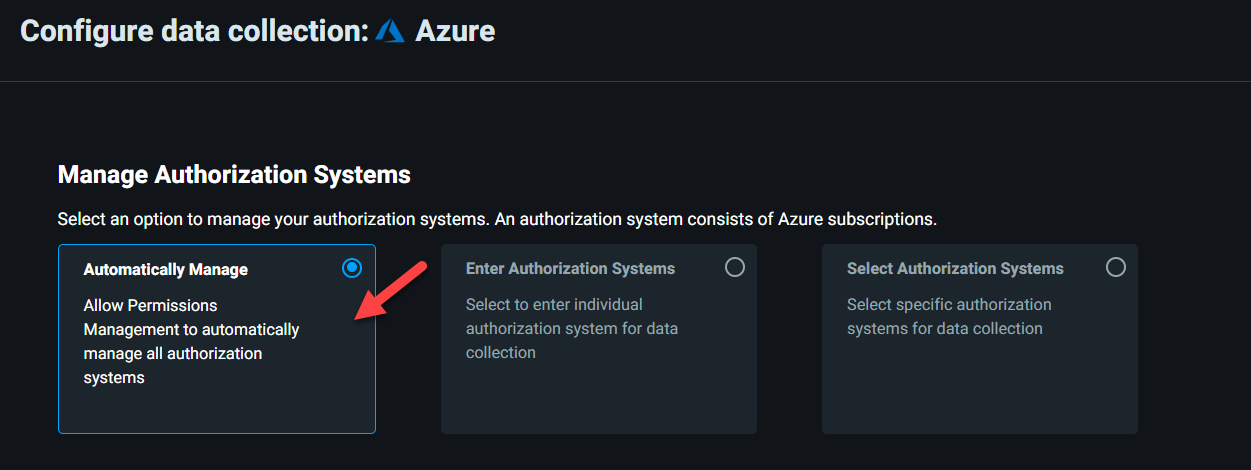
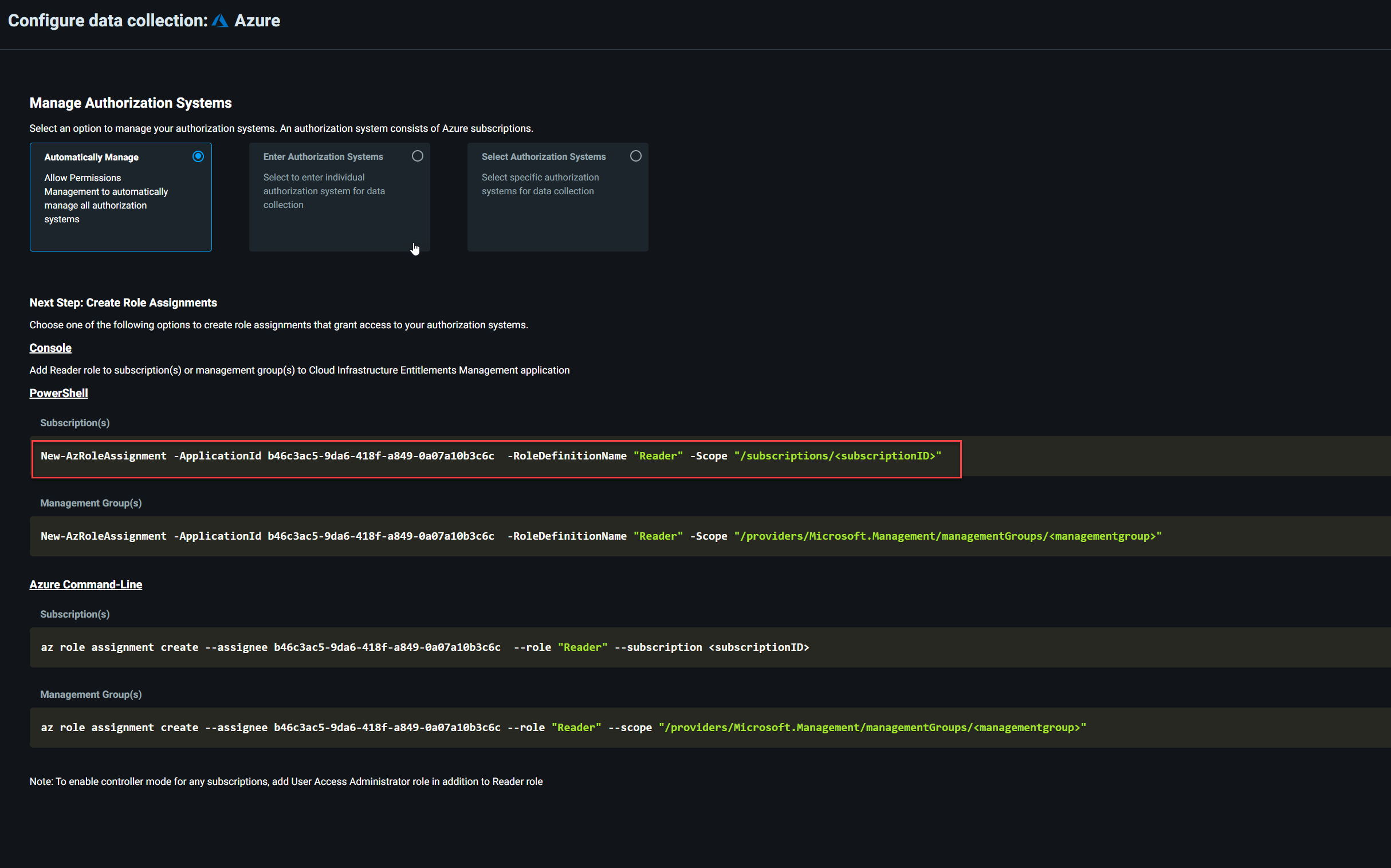
6) In this demo, I am going to use the Automatically Manage option for onboarding. This will allow current and future subscriptions to be automatically detected and monitored.
7) In there we can see a list of PowerShell and CLI commands that we can use to grant reader role to Cloud Infrastructure Entitlement Management application at the management group or subscription level. As I am going to use it at the subscription level, I am going to use,
New-AzRoleAssignment -ApplicationId b46c3ac5-9da6-418f-a849-0a07a10b3c6c
-RoleDefinitionName “Reader” -Scope “/subscriptions/<subscriptionID>”
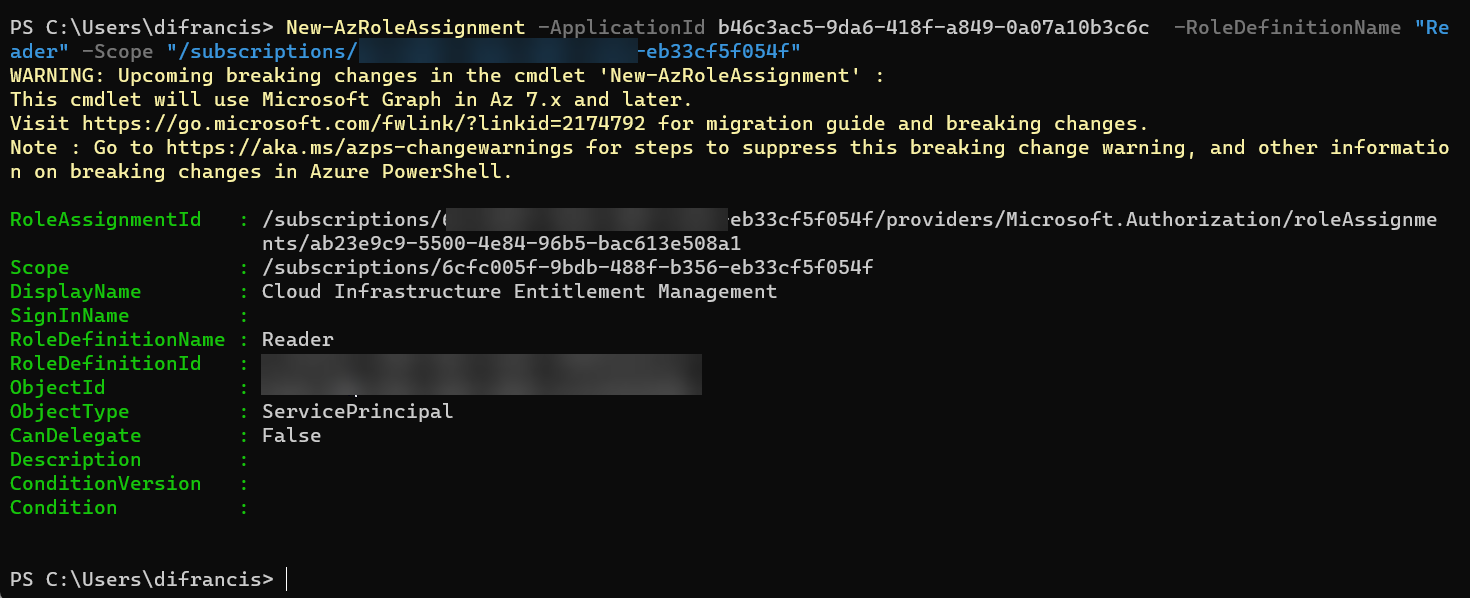
8) I connected to the tenant using Azure Powershell and run the command.
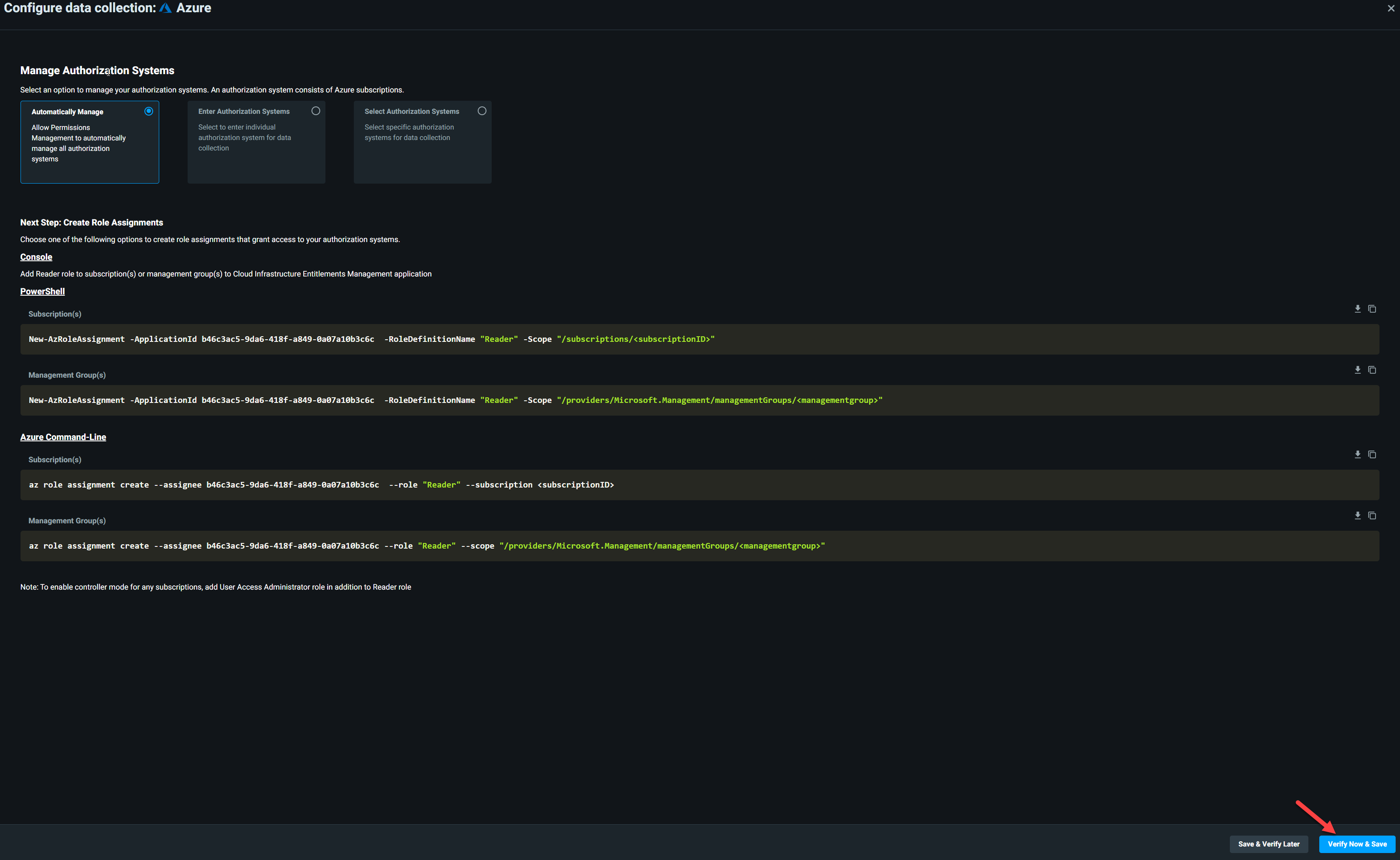
9) Then click on Verify Now & Save
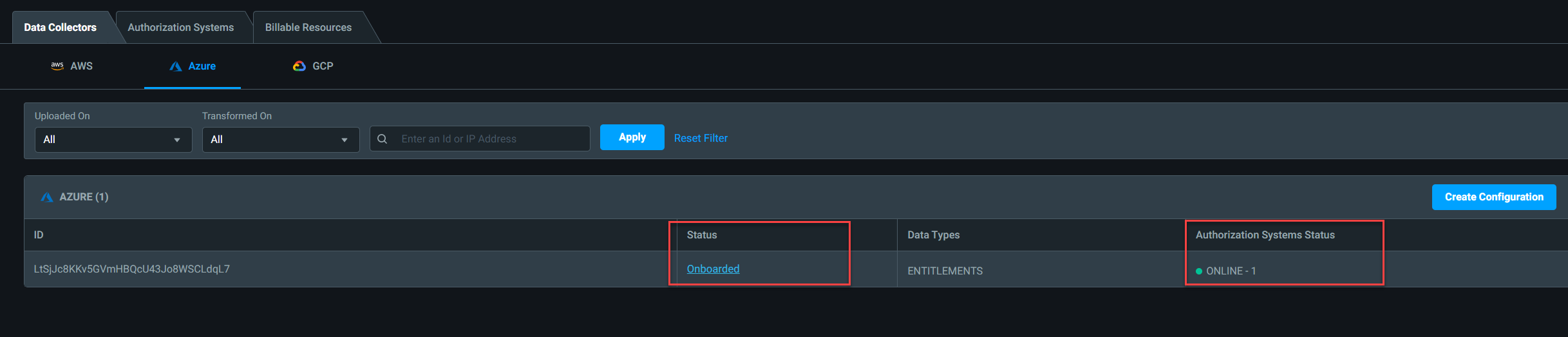
10) After a few minutes we can see the connection status is showing as “Onboarded” and the Authorization system status is “Online”
As we can see the subscription is now onboarded successfully. In the next article let’s explore what Microsoft Entra Permissions Management discovered. This marks the end of this blog post, If you have any further questions, feel free to contact me at rebeladm@live.com.