In my previous post I explain how we can use Azure AD B2B to share services/resources between organization. Once these B2B users are register with Azure AD, we can apply “Conditional Access” polcies to control their access further. In this demo I am going to show how to do that.
Prerequisites
Before we start please go ahead and read my previous article about Azure AD B2B, because in this post I am going assume that you already finish the sign-up process for Azure AD B2B users.
You can access the post using http://www.rebeladmin.com/2018/11/cross-organization-collaboration-azure-ad-b2b/
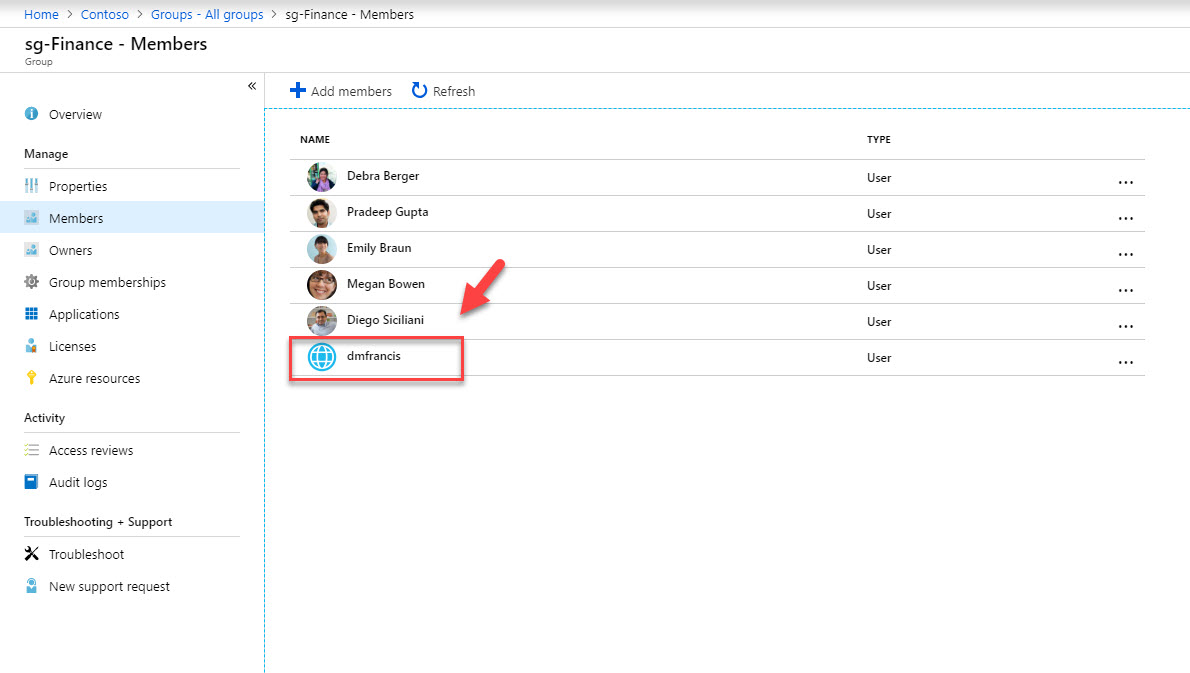
In my demo environment, I have sg-Finance security group. All the users from Finance department are part of it. I do have several applications assigned to them. Company Contoso recently made partnership with another company. Some privileged users from this new company required access to the applications used by sg-Finance users. Therefore, I went ahead and made them member of this group using Azure B2B. However, I need to put extra layer of security for these external user access requests to make sure my sensitive data been protected.
1. To start the configuration, I am logging in to https://portal.azure.com as Global Administrator
2. Then Azure Active Directory | Groups | sg-Finance | Members. In here I can see B2B user dmfrancis
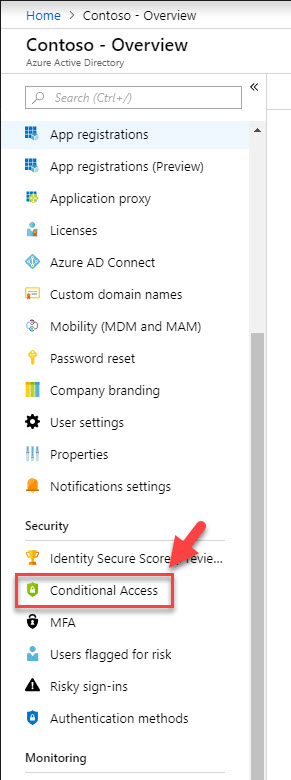
3. Now go back to Azure Active Directory home page and click on Conditional Access
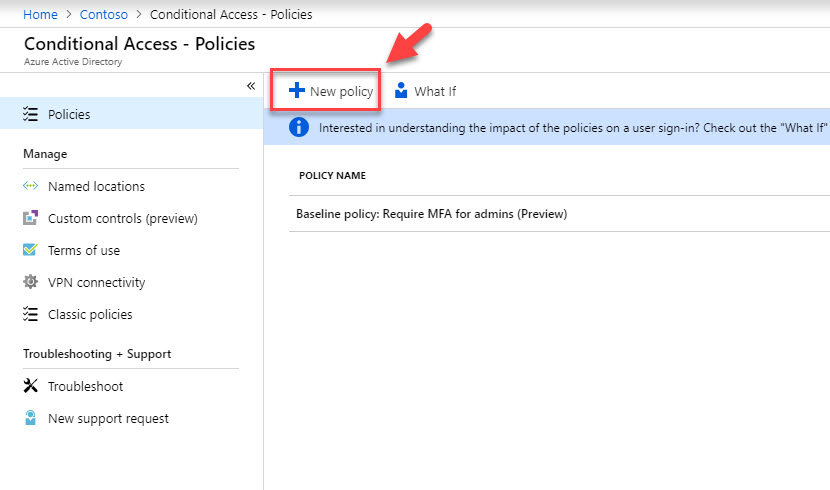
4. Then click on New policy
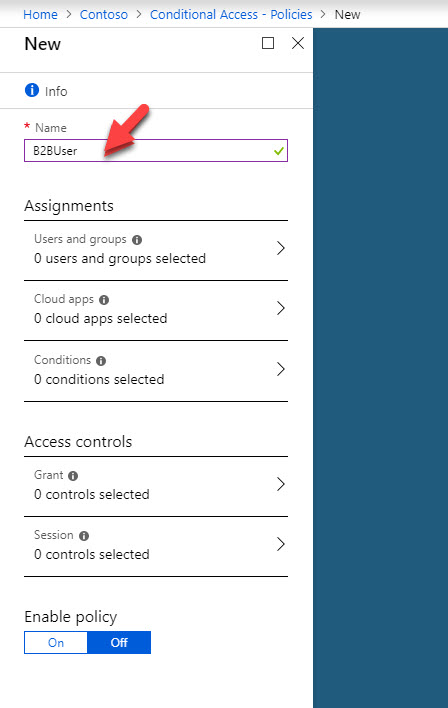
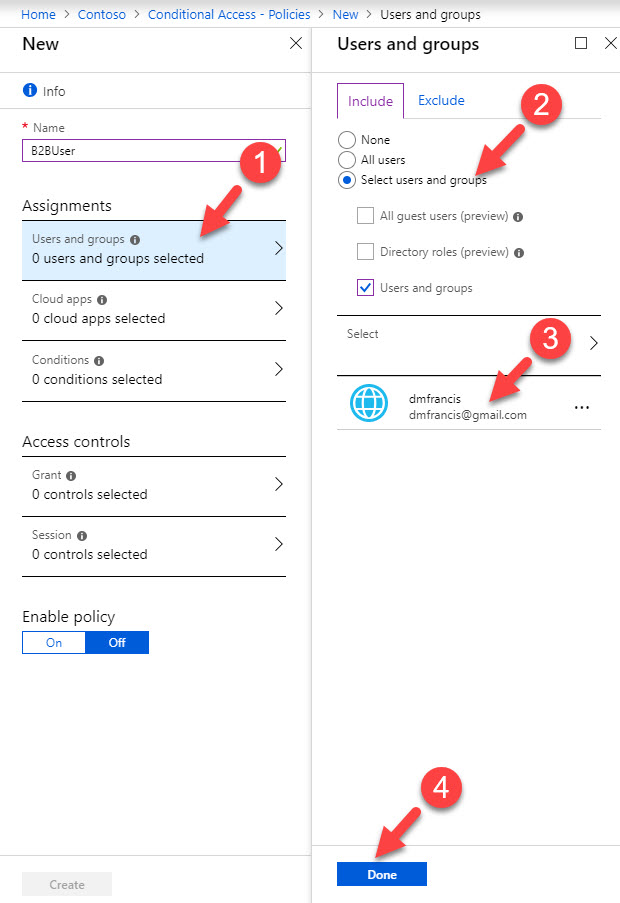
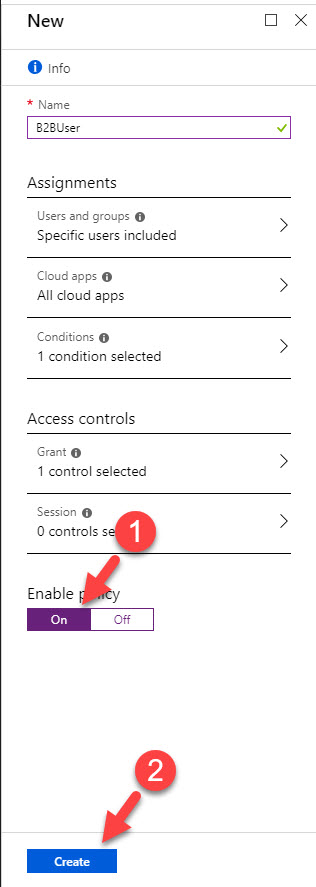
5. It opens up policy wizard, first define name for the policy.
6. Then click on Assignments and select the B2B user. If you have multiple users, it is best to create a group and then apply policy to it.
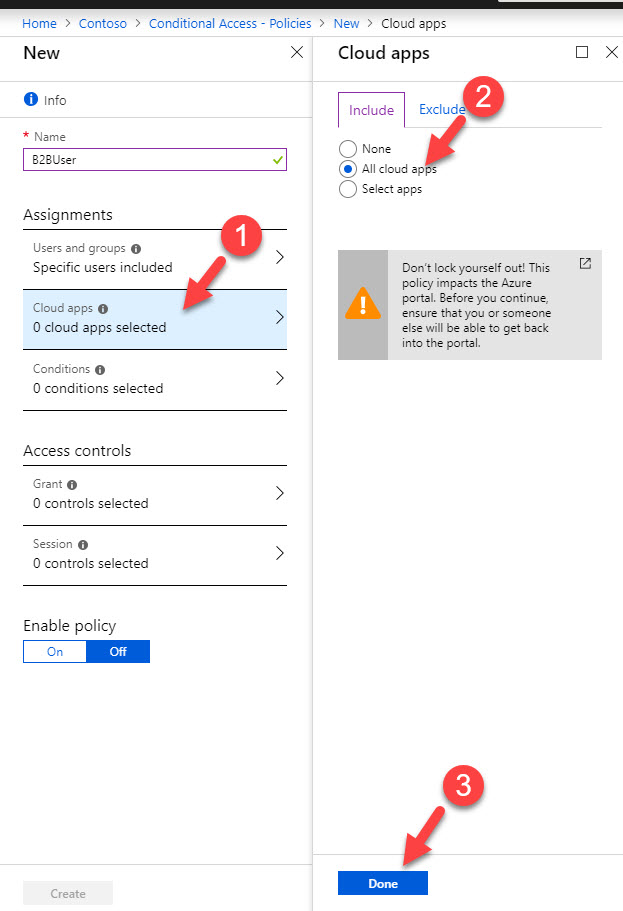
7. As next step, under cloud apps I am selecting All apps.
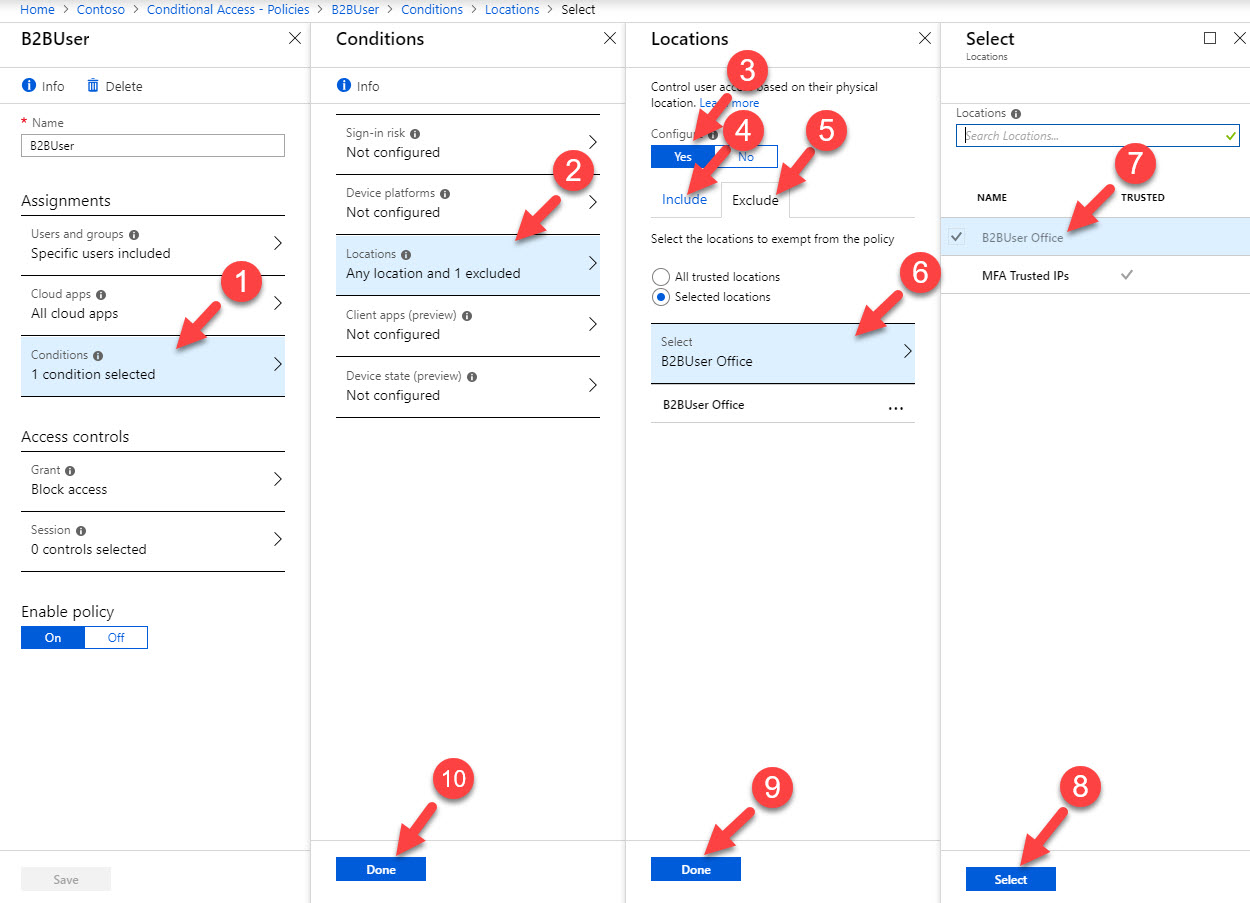
8. Then under the conditions click on Locations and then click on Yes to enable the policy. Then click on Any location. After, click on Exclude and select the B2B office location.
[su_note]You can create named locations under Conditional access | Named locations , you need to create it first before use in a policy. [/su_note]
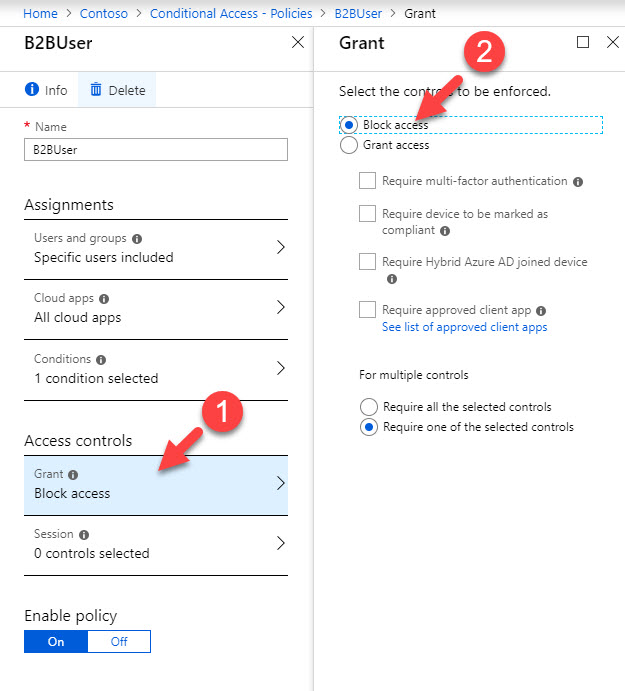
9. Under access controls click on Grant and then select Block access. So the idea is to block any access except the connections comes from trusted B2B user office.
10. At the end click On under enable policy and then click create to activate the policy.
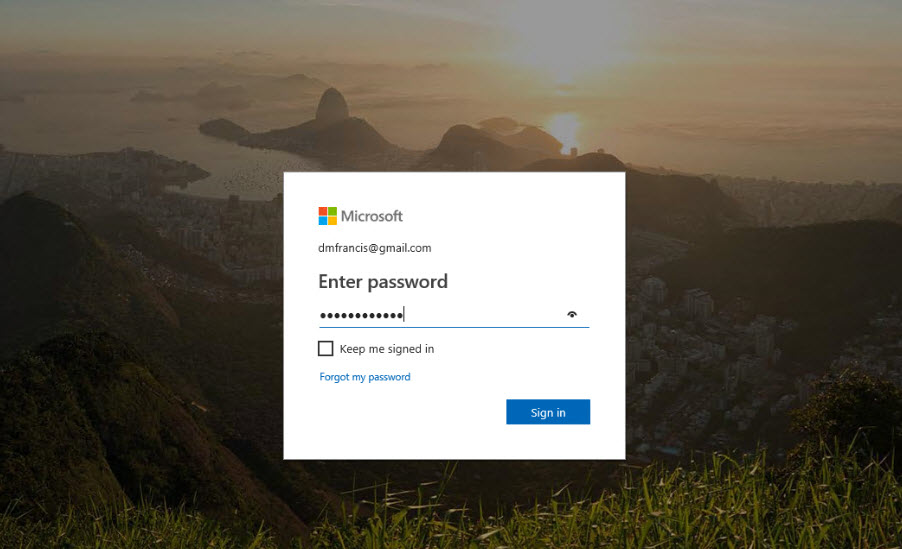
11. Now we done with the configuration, let’s go ahead and test it. To start, I am logging in to http://myapps.microsoft.com as B2B user from B2B user’s office.
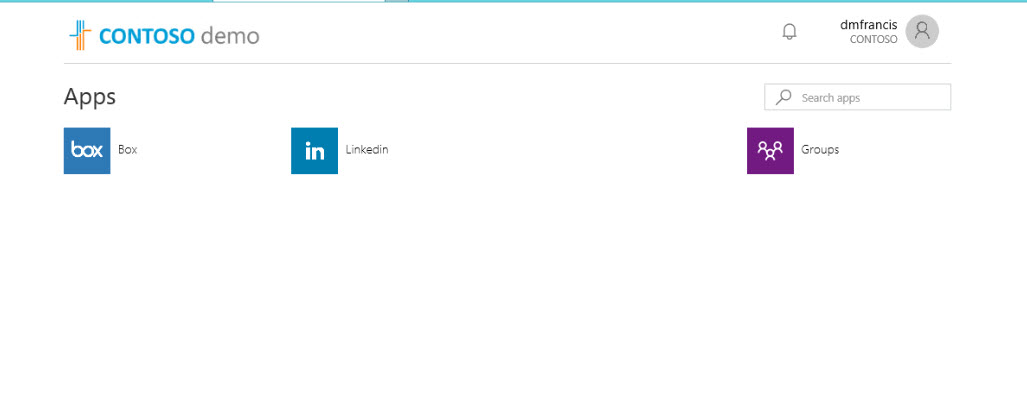
12. After login verification, user was able to login successfully.
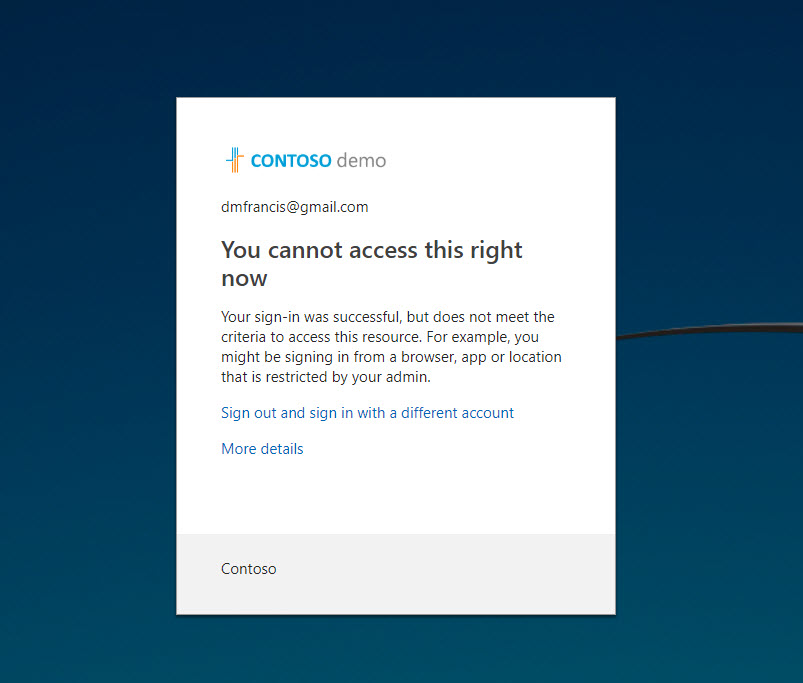
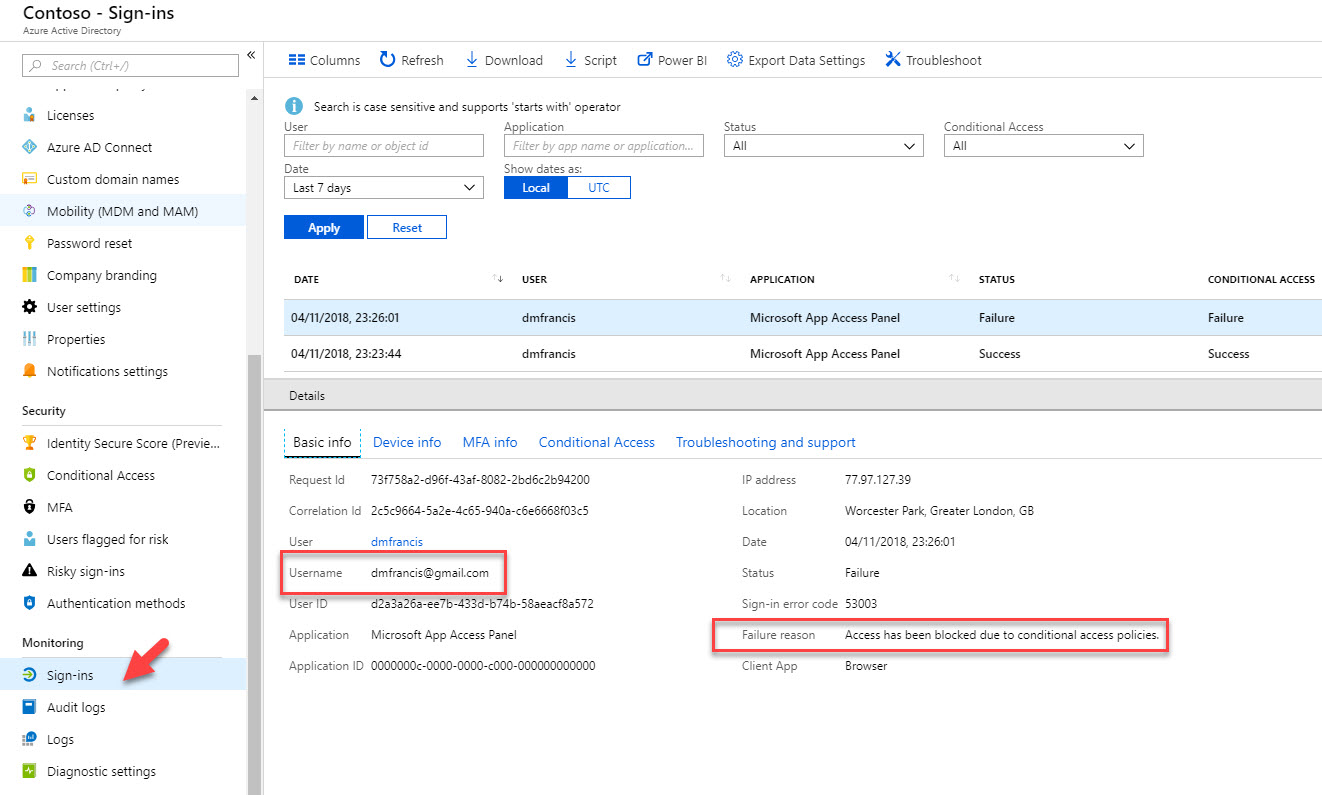
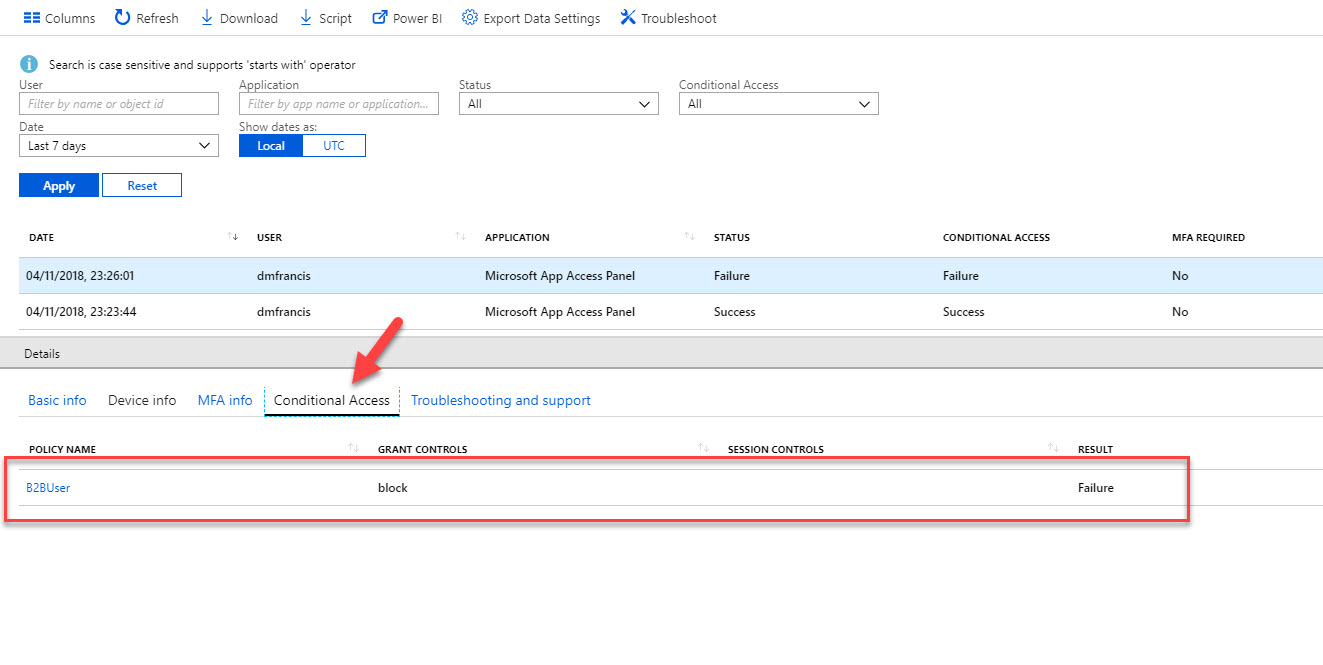
13. Now let’s try to login from different location. As soon as I try to login I gets the following error. It means policy is working as expect.
14. Then if we go to Azure Active Directory home page | Sign-ins, we can see the failure and the reason behind it.
As we can see we can access Azure conditional access policies to further control access requests from Azure B2B users. This marks the end of this blog post. If you have any further questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.