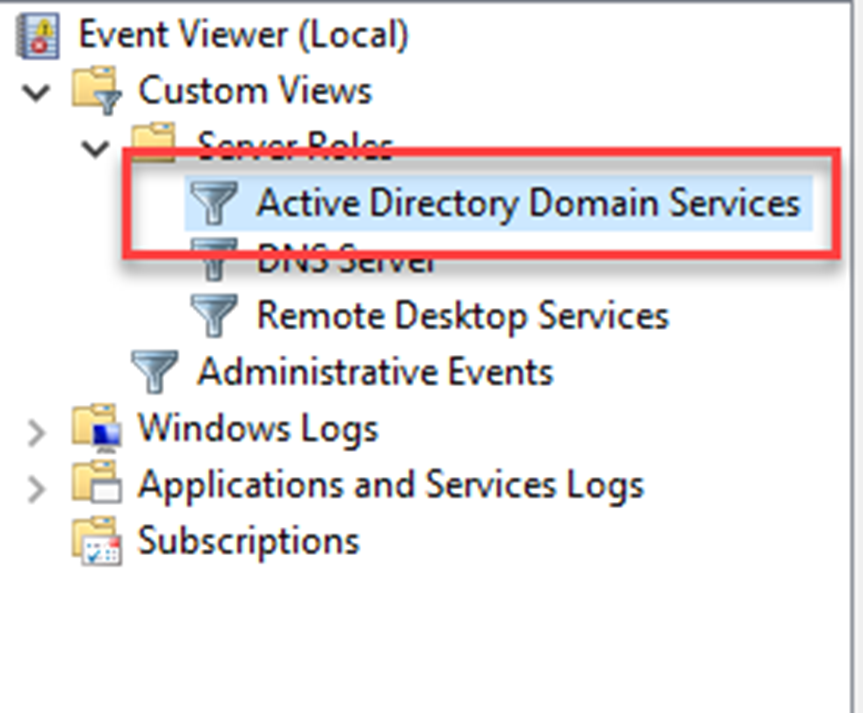
There are different ways to review Active Directory service related logs in a domain controller. Most common way is to review events under Event Viewer mmc.
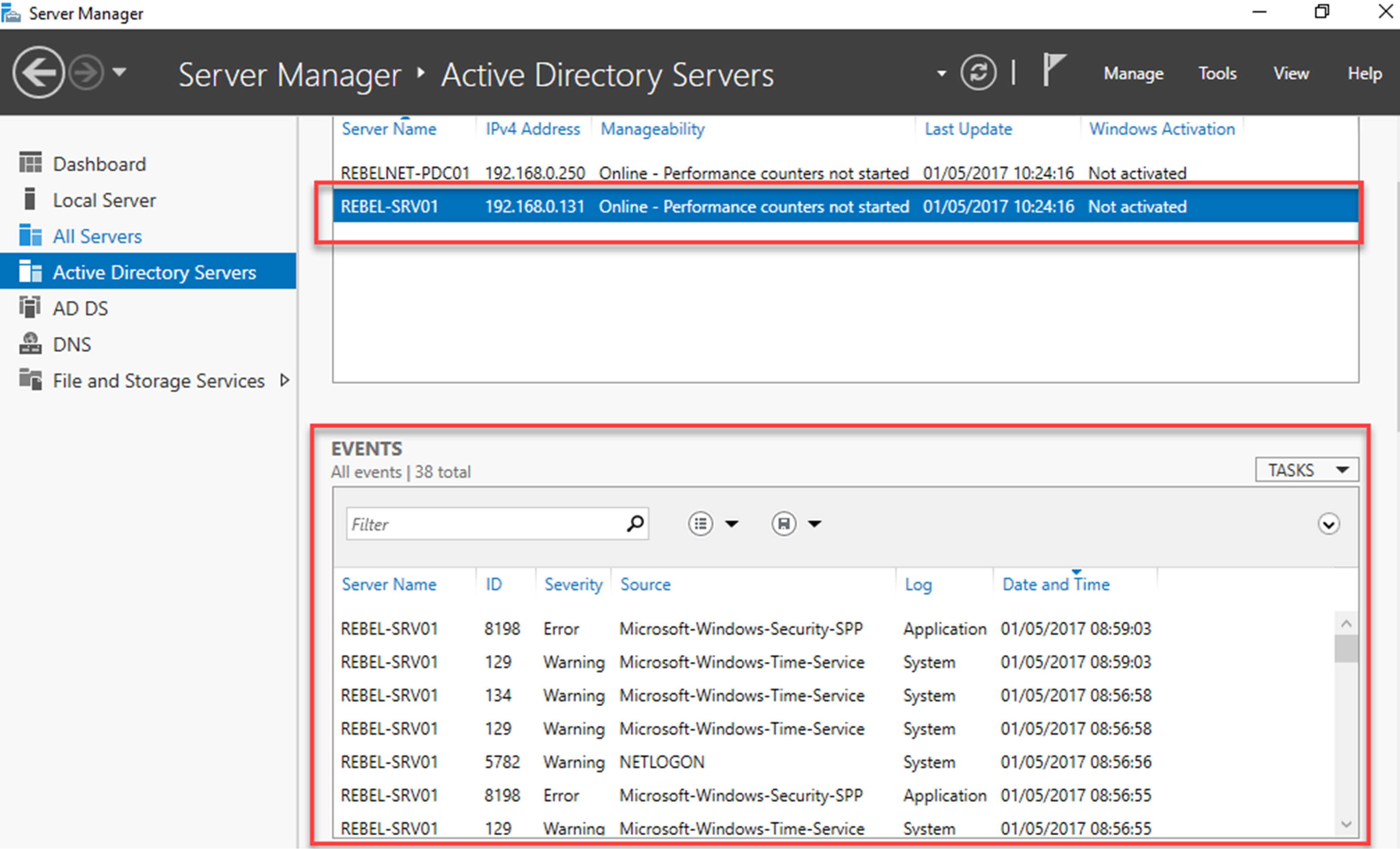
We can review events using server manager too.
We also can use PowerShell commands to review event logs or filter events from local and remote computers without any additional service configurations. Get-EventLog is the primary cmdlet we can use for this task.
Get-EventLog -List
Above command will list down the details about the log files in your local system including the log file name, max log file size, number of entries.
Get-EventLog -LogName ‘Directory Service’ | fl
Above command will list down all the events under the log file Directory Service
we also can limit the number of events we need to list down. As an example, if we only need to list down the latest 5 events from the Directory Service log file, we can use,
Get-EventLog -Newest 5 -LogName ‘Directory Service’
We can further filter down it by listing down evens according to entry type.
Get-EventLog -Newest 5 -LogName ‘Directory Service’ -EntryType Error
Above command will list down first five “errors” in the Directory Service log file.
We also can add time limit to filter events more.
Get-EventLog -Newest 5 -LogName ‘Directory Service’ -EntryType Error –After (Get-Date).AddDays(-1)
Above command will list down the events with error type ‘error’ with in last 24 hours under Directory Service log.
We also can get the events from the remote computers.
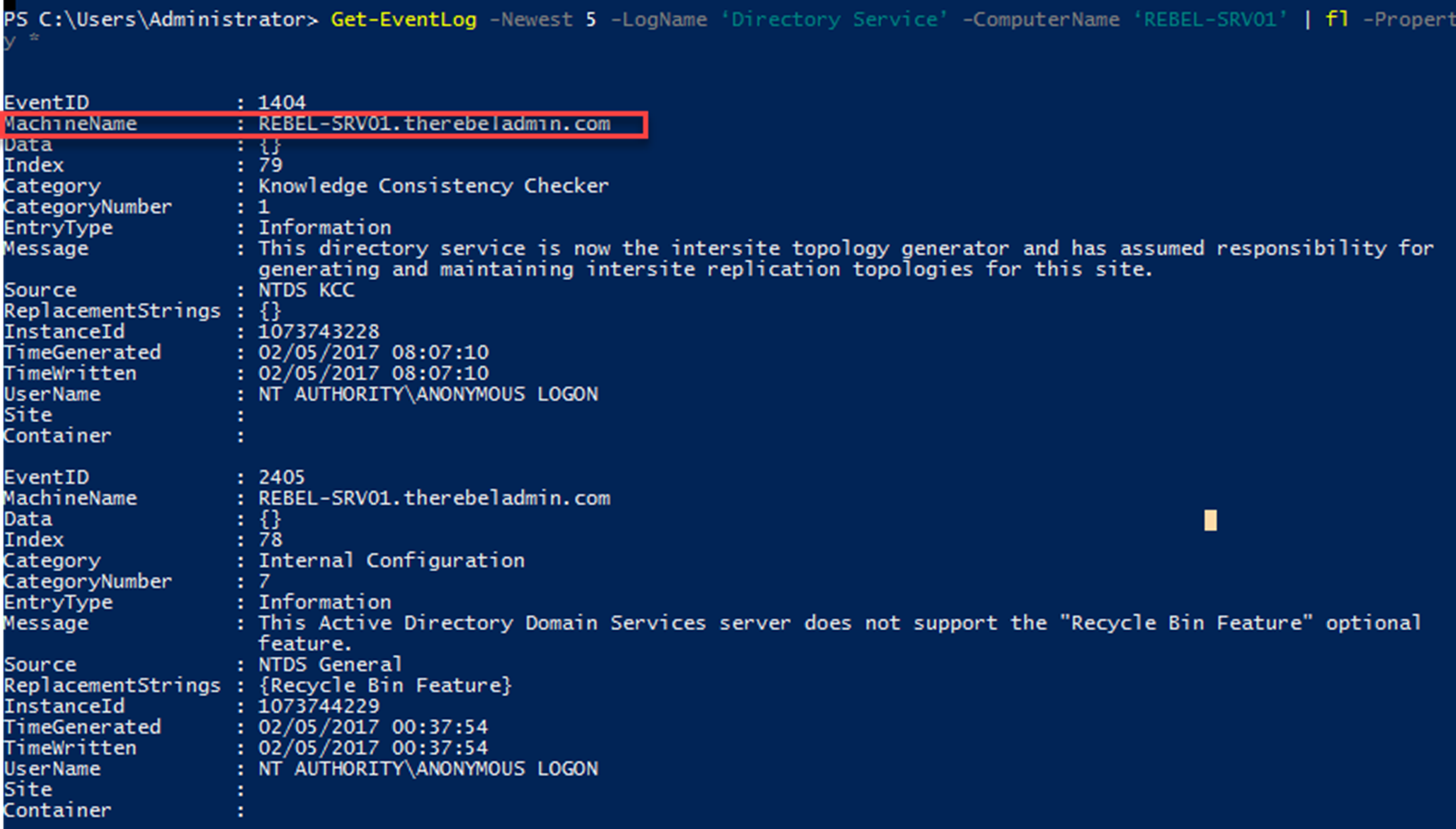
Get-EventLog -Newest 5 -LogName ‘Directory Service’ -ComputerName ‘REBEL-SRV01’ | fl -Property *
Above command will list down the first five log entries in Directory Service log file from REBEL-SRV01 remote computer.
We also can extract events from few computers in same time.
Get-EventLog -Newest 5 -LogName ‘Directory Service’ -ComputerName “localhost”,“REBEL-SRV01”
Above command will list down the log entries from local computer and the REBEL-SRV01 remote computer.
When it comes to filtering, we can further filter events using the event source.
Get-EventLog -LogName ‘Directory Service’ -Source “NTDS KCC”
Above command will list down the events with the source NTDS KCC
It also allows to search for the specific event ids.
Get-EventLog -LogName ‘Directory Service’ | where {$_.eventID -eq 1000}
Above command will list down the events with event id 1000.
Note – There are recommended list of events which we need to audit periodically to identify potential issues in active directory environment. The complete list is available for review under https://docs.microsoft.com/en-gb/windows-server/identity/ad-ds/plan/appendix-l–events-to-monitor
This marks the end of this blog post. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts.