Last Updated on June 30, 2014 by Dishan M. Francis
in a parent-child domain environment there will be different child domains which connected with the HQ main servers. By default due to the trust relationship between child and parent domains users can log in to different domains resources using their logins. For ex- an employee in HQ will be able to log in to sales child domain with his login credentials which used in HQ. But in occassions this need to be restricted and they may only need to be allowed to log in to their corresponding domain (parent or child ) resources only. But roles such as system manager, network administrators etc. will need to be having these features to use for company operations.
By default the resources are allowed to login for all the users in “Domain Admins”, “Domain users”, “Administrators”, “Authenticated Users” groups.
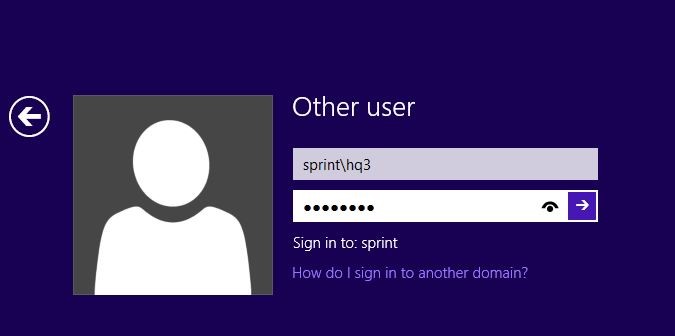
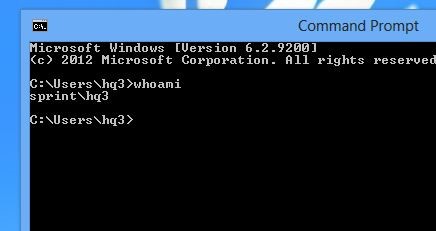
For the demonstration I have setup parent domain called sprint.local and child domain called sales.sprint.local. In here I am going to show how we can block access to pcs in child domain from the parent domain. As I mentioned because of the trust between domains, by default users in parent domain will be log in to pc in child domain just using his credentials without any issues. I am log in to pc in sales.sprint.local called TESTPC using user “hq3” from Parent Domain.
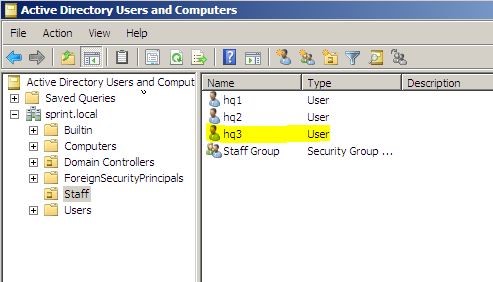
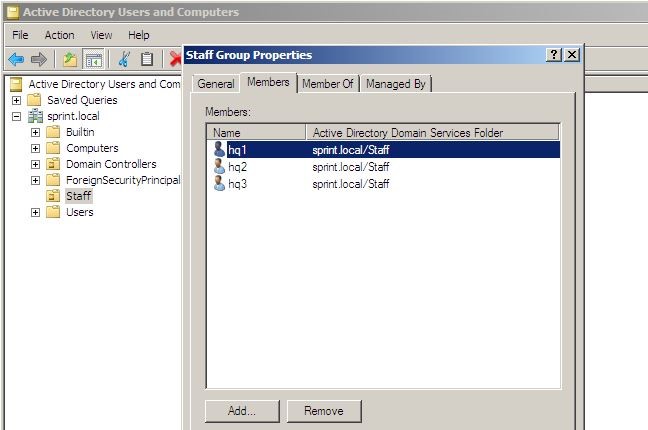
As the next step I have created new security group called “Staff Group” in sprint.local Parent domain and add hq1,hq2, and recently tested user hq3 to it. Here I am not going to give every step as in previous steps I have showed how to create a group.
Now we need to go in to the child domain sales.sprint.local and create the group policy to block the access from parent domain’s “Staff Group”.
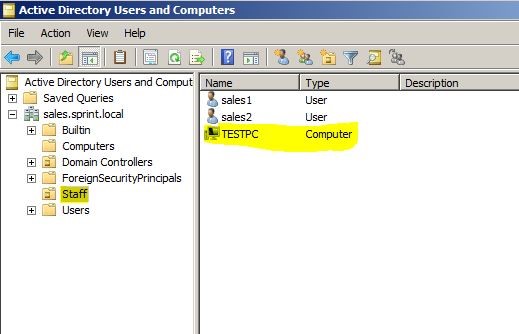
In Sales.sprint.local child domain we have Organization Unit Called “Staff” and the TESTPC is in the staff OU.
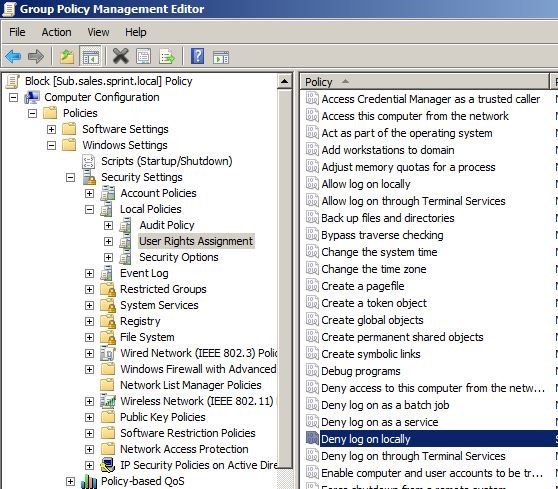
Now let’s open up the “Group Policy Management” snap in in administrative tools.
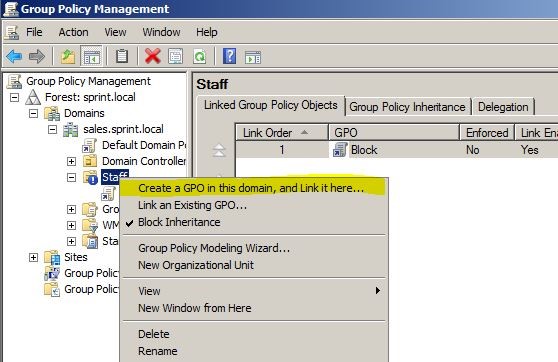
Once it open expand the domain tree and go to “Staff” OU then right click on it and select “Create GPO in this domain and link it here”. In here you will see I had selected “Block Inheritance” option already, it is just to prevent group policy inheritance from top level to prevent any conflict on demonstration. This feature can use depend on the situation.
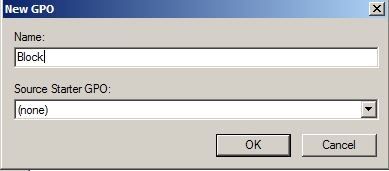
In next window choose appropriate name and click ok.
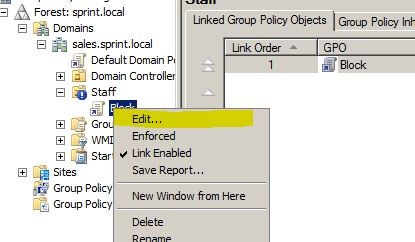
Once it’s added right click on new policy and click on edit to go to policy edit window.
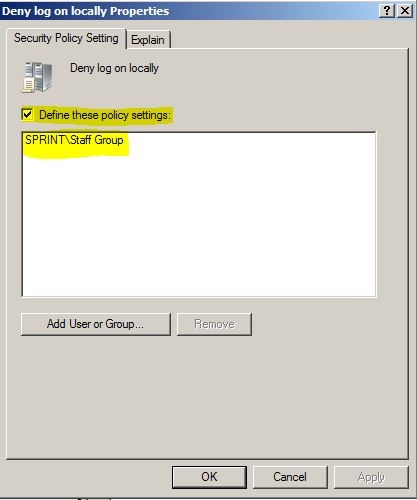
In the policy editor go to computer configurations > windows settings > local policies > user rights assignment. Then from the list double click on “Deny Log on Locally” option.
Then once it open, click on “define these policy settings” and then click “add user or group” button to add the “Sprint\Staff Group” to it.
Click ok to apply the change. Then we ready with the policy so it should block the access permissions to sales.sprint.local domain from parent domain’s “Staff Group”.
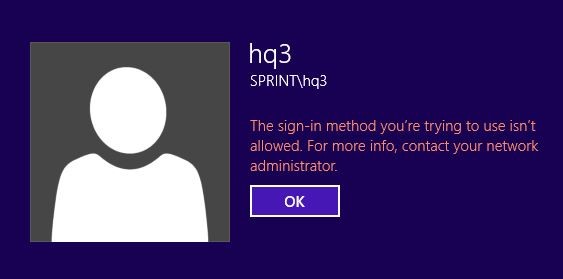
To test it out first I restarted the TESTPC on sales.sprint.local domain to apply the group policies. And then I was trying to log in to the pc as sprint\hq3.
Then right away it gave the error saying it’s not permitted.
So the method was success and we were able to prevent access from sprint\staff group which by default had access permissions.
This is just demo and we can use this efficiency with the department requirements to block the group. With this it only block access to the users in sprint\ staff group and all others can still log in.